Google Wallet adds ‘Verification settings’ to balance security and convenience
What you need to know
- Google Wallet has added a new verification settings menu for Android devices.
- This setting allows users to decide whether or not they need to be verified before paying for a ticket on public transport.
- This will help to make Google Wallet even more secure.
The ability to store card details, transit passes, boarding passes, and contactless payments, means Google Wallet is a convenient way to save time. Now, Google is working hard to make Wallet even more secure and user-friendly by introducing a new ‘Verification settings’ menu.
The new addition, as spotted by 9to5 Google, lets users decide whether or not verification is required, specifically when paying for a transit ticket. Under “Wallet settings” is the new “Security” heading, under which “Verification settings” are listed. When selected, the user can “choose if you’ll need to verify it’s you when using your items stored in Wallet.”
At the moment, the only available option here is “Transit payments.” When the “verification required” toggle is on, Wallet will require “verification for paying for bus, metro, and more with a credit or debit card.” This means the usual options for a device include a PIN or fingerprint scan, for example.
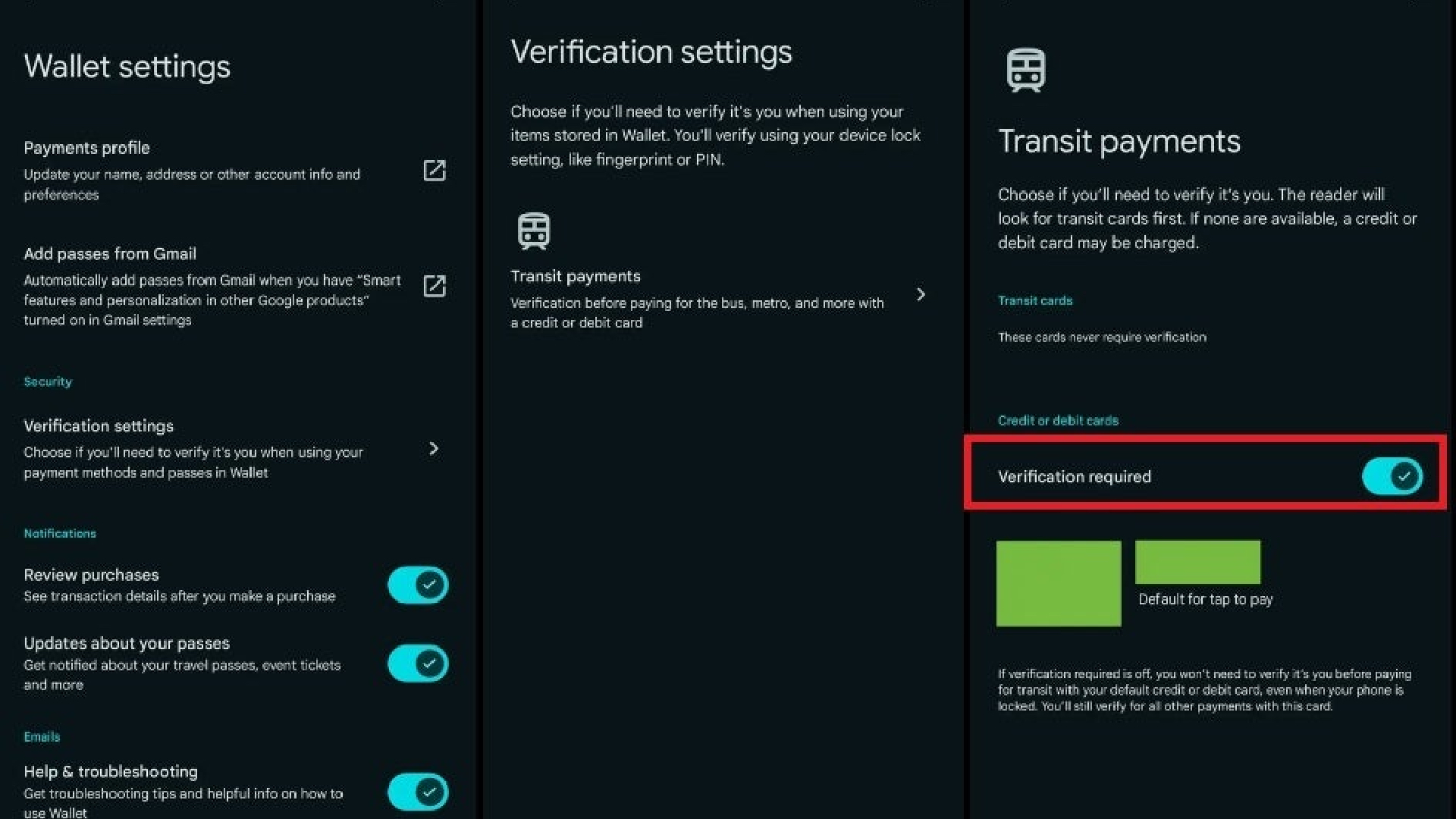
If a user already has a transit pass stored in Wallet, the toggle will be switched on by default. The wallet will then require verification before paying with their bank card. If no transit pass is stored, this option will be automatically turned off.
This means that anyone without a transit pass can quickly pay for their ticket without needing to verify themselves. Users can, however, switch it on even if they don’t have a transit pass if they want that added security.
Importantly, this feature is only applicable to paying for transit. As it says underneath the toggle: “You’ll still verify for all other payments with this card.” This means that even if you disable the setting, it won’t allow someone to swipe your phone and go wild with your credit card. Although, they may get to enjoy a day out on your local metro system.
The new setting is available in version 24.10 of Google Wallet. It’s another…