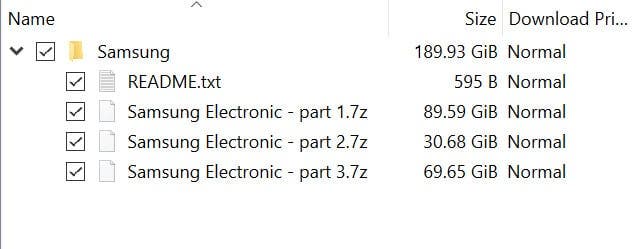
190GB of data stolen and published
There seems to be no respite in the digital world and the Lapsus group is again the protagonist after the NVIDIA case last week. The victim in this case is Samsung which has been the subject of a huge theft of information that has been published on Torrent, potentially putting millions of Samsung smartphones at risk.
The information that would have been stolen and published would involve:
- Source code for every Trusted Applet (TA) installed in Samsung’s TrustZone environment used for sensitive operations (e.g. hardware cryptography, binary encryption, access control)
- Algorithms for all biometric unlock operations
- Bootloader source code for all recent Samsung devices
- Confidential source code from Qualcomm
- Source code for Samsung’s activation servers
- Full source code for technology used for authorizing and authenticating Samsung accounts, including APIs and services
Unlike the Nvidia case, however, the 190GB of data stolen from Samsung were available entirely on torrents. The attack is very dangerous since the TrustZone area of Samsung holds very sensitive information.

Samsung under hacker attack: 190GB of data stolen and published
Furthermore, having the source code available could allow hackers to find security holes even before Samsung can close them (there is no 100% secure system and 0-days updates are proof of this).
The publication of all the material is still strange since, in general, these hackers ask for a ransom; and only in case of non-payment do they publish the material in their possession. We will see if there will be any news in the next few hours/days; but it is clear that the story will have an important following; and Samsung will have to find new ways to protect the data of millions of potential users.
Regarding NVIDIA, last Friday the company had confirmed that it had started investigations relating to an “incident” related to the malfunction of certain services; including the internal email system and certain tools for developers, without elaborating further; however, according to internal Telegraph sources; an intrusion into the company’s computer systems would have occurred in the two days before; which would have “completely…