Active Threat Alerts
Preventing Web Application Access Control Abuse
SUMMARY
The Australian Signals Directorate’s Australian…
July 28, 2023/by SecureTechThe Australian Signals Directorate’s Australian…
Threat Actors Exploiting Citrix CVE-2023-3519 to Implant Webshells
SUMMARY
The Cybersecurity and Infrastructure Security…
July 21, 2023/by SecureTechThe Cybersecurity and Infrastructure Security…
Enhanced Monitoring to Detect APT Activity Targeting Outlook Online
SUMMARY
In June 2023, a Federal Civilian Executive…
July 13, 2023/by SecureTechIn June 2023, a Federal Civilian Executive…
Increased Truebot Activity Infects U.S. and Canada Based Networks
SUMMARY
The Cybersecurity and Infrastructure Security…
July 7, 2023/by SecureTechThe Cybersecurity and Infrastructure Security…
Understanding Ransomware Threat Actors: LockBit
SUMMARY
In 2022, LockBit was the most deployed ransomware…
June 15, 2023/by SecureTechIn 2022, LockBit was the most deployed ransomware…
#StopRansomware: CL0P Ransomware Gang Exploits CVE-2023-34362 MOVEit Vulnerability
SUMMARY
Note: this joint Cybersecurity Advisory…
June 8, 2023/by SecureTechNote: this joint Cybersecurity Advisory…
People’s Republic of China State-Sponsored Cyber Actor Living off the Land to Evade Detection
The United States and international cybersecurity…
May 24, 2023/by SecureTech#StopRansomware: BianLian Ransomware Group | CISA
Summary
Note: This joint Cybersecurity Advisory…
May 17, 2023/by SecureTechNote: This joint Cybersecurity Advisory…
Malicious Actors Exploit CVE-2023-27350 in PaperCut MF and NG
SUMMARY
The Federal Bureau of Investigation (FBI)…
May 12, 2023/by SecureTechThe Federal Bureau of Investigation (FBI)…
Hunting Russian Intelligence “Snake” Malware
SUMMARY
The Snake implant is considered the most…
May 10, 2023/by SecureTechThe Snake implant is considered the most…
APT28 Exploits Known Vulnerability to Carry Out Reconnaissance and Deploy Malware on Cisco Routers
APT28 accesses poorly maintained Cisco routers and…
April 18, 2023/by SecureTech#StopRansomware: LockBit 3.0 | CISA
SUMMARY
Note: this joint Cybersecurity Advisory…
March 16, 2023/by SecureTechNote: this joint Cybersecurity Advisory…
Threat Actors Exploit Progress Telerik Vulnerability in U.S. Government IIS Server
SUMMARY
From November 2022 through early January…
March 15, 2023/by SecureTechFrom November 2022 through early January…
#StopRansomware: Royal Ransomware | CISA
SUMMARY
Note: This joint Cybersecurity Advisory…
March 3, 2023/by SecureTechNote: This joint Cybersecurity Advisory…
CISA Red Team Shares Key Findings to Improve Monitoring and Hardening of Networks
SUMMARY
The Cybersecurity and Infrastructure Security…
March 2, 2023/by SecureTechThe Cybersecurity and Infrastructure Security…
#StopRansomware: Ransomware Attacks on Critical Infrastructure Fund DPRK Malicious Cyber Activities
Note: This Cybersecurity Advisory (CSA) is part of an ongoing…
February 9, 2023/by SecureTech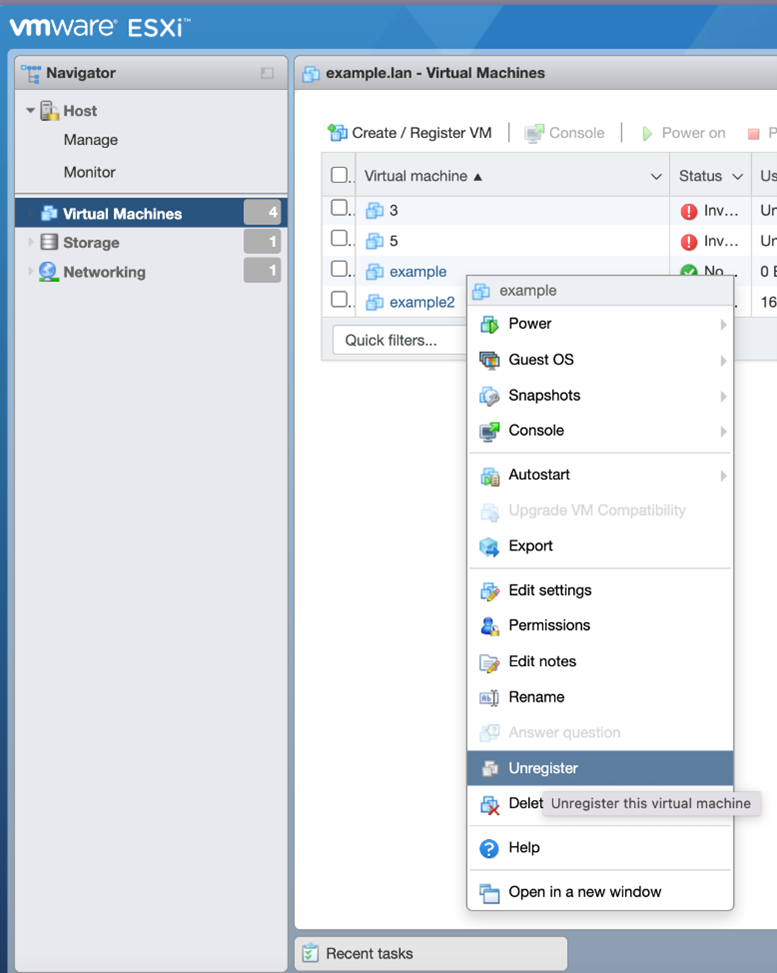
ESXiArgs Ransomware Virtual Machine Recovery Guidance
The Cybersecurity and Infrastructure Security Agency (CISA)…
February 8, 2023/by SecureTech
Protecting Against Malicious Use of Remote Monitoring and Management Software
The Cybersecurity and Infrastructure Security Agency (CISA),…
January 26, 2023/by SecureTech#StopRansomware: Cuba Ransomware | CISA
Summary
Actions to take…
December 2, 2022/by SecureTechActions to take…
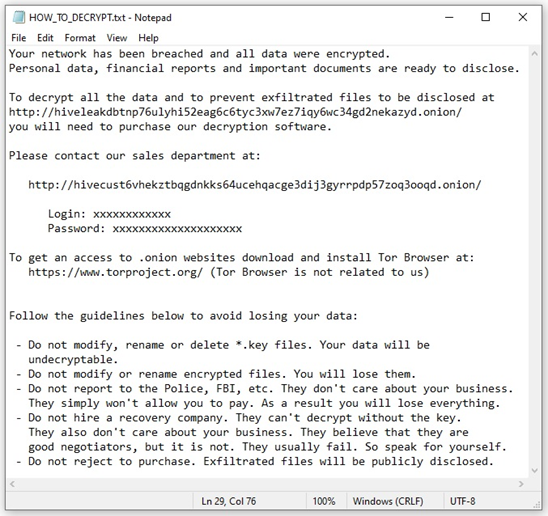
#StopRansomware: Hive Ransomware | CISA
Summary
Actions to Take…
November 17, 2022/by SecureTechActions to Take…
Iranian Government-Sponsored APT Actors Compromise Federal Network, Deploy Crypto Miner, Credential Harvester
From mid-June through mid-July 2022, CISA conducted an incident…
November 16, 2022/by SecureTech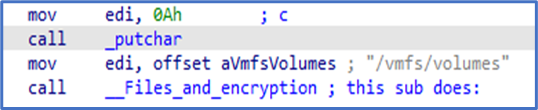
#StopRansomware: Daixin Team | CISA
Summary
Actions to take…
October 21, 2022/by SecureTechActions to take…
Top CVEs Actively Exploited By People’s Republic of China State-Sponsored Cyber Actors
Summary
This joint Cybersecurity…
October 7, 2022/by SecureTechThis joint Cybersecurity…
Impacket and Exfiltration Tool Used to Steal Sensitive Information from Defense Industrial Base Organization
Actions to Help Protect Against APT Cyber Activity:• Enforce…
October 5, 2022/by SecureTechControl System Defense: Know the Opponent
Traditional approaches to securing OT/ICS do not adequately…
September 23, 2022/by SecureTech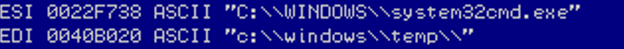
Iranian State Actors Conduct Cyber Operations Against the Government of Albania
The Federal Bureau of Investigation (FBI) and the Cybersecurity…
September 22, 2022/by SecureTech