Alleviating BlackEnergy-Enabled DDoS Attacks
BlackEnergy first appeared in 2007. Designed to launch distributed denial-of-service (DDoS) attacks or download customized spam or banking data-stealer plug-ins, it was again used to target the State Bar of Georgia last May.
Following the most recent cyber attack, the office had to suspend normal operations until the issue was addressed. Investigations that ensued soon after the incident revealed the use of BlackEnergy along with the identification of eight domains—clusteron[.]ru, svdrom[.]cn, funpic[.]org, logartos[.]org, pizdos[.]net, weberror[.]cn, h278666y[.]net, and inattack[.]ru—as indicators of compromise (IoCs).
Using these web properties as jump-off points for a deep dive enabled by WHOIS and Domain Name System (DNS) data led to the discovery of:
- 49 IP addresses to which the domains identified as IoCs resolved
- Two unredacted email addresses used to register the domains tagged as IoCs
- 6,003 domains that shared the IoCs’ registrant email addresses or IP addresses, 141 of which were dubbed “malicious” by various malware engines
A sample of the additional artifacts obtained from our analysis is available for download from our website.
Expanding the List of IoCs for Better Protection
To help organizations to protect their networks from BlackEnergy-enabled attacks, we identified as many possibly related artifacts with WHOIS and DNS data.
Using the IoC domains identified as DNS lookup search terms led to the discovery of 49 IP addresses to which they resolved. These were spread across 11 countries led by the U.S., Netherlands, Russia, Germany, and Singapore.
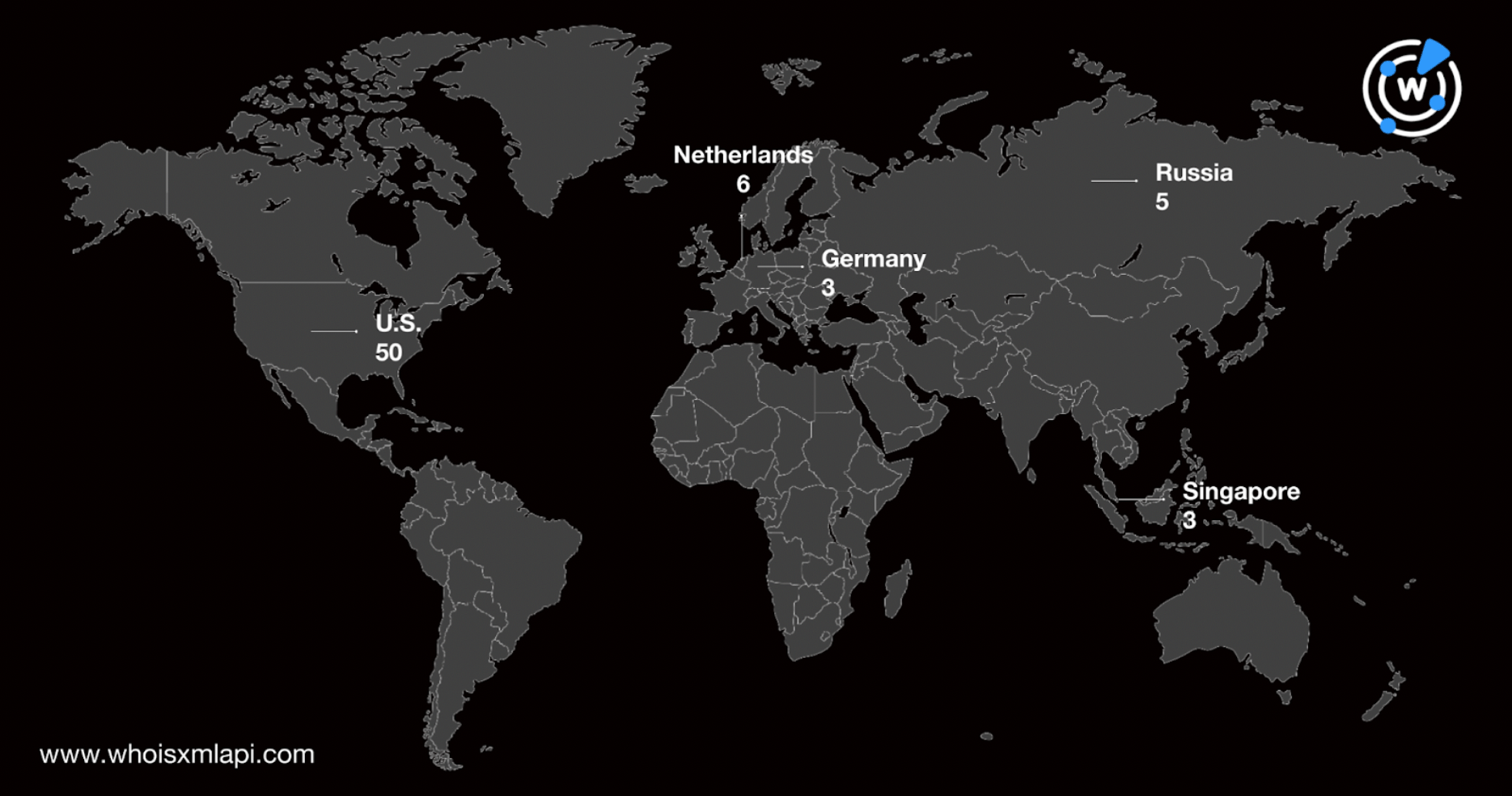
While none of the IP addresses are currently considered dangerous as per malware checks we conducted, monitoring them for signs of malicious activity may still be worth doing as some of them served as shared hosts to the IoCs.
A closer scrutiny of the historical WHOIS records of the domains tagged as IoCs, meanwhile, allowed us to uncover two unredacted email addresses—135224*****@163[.]com and asdf9*****@21cn[.]com—used to register them.
Reverse IP and reverse WHOIS lookups using the IP addresses and email addresses, respectively, as search terms further provided 6,003 possibly connected…

