Android malware Escobar steals your Google Authenticator MFA codes

The Aberebot Android banking trojan has returned under the name ‘Escobar’ with new features, including stealing Google Authenticator multi-factor authentication codes.
The new features in the latest Aberebot version also include taking control of the infected Android devices using VNC, recording audio, and taking photos, while also expanding the set of targeted apps for credential theft.
The main goal of the trojan is to steal enough information to allow the threat actors to take over victims’ bank accounts, siphon available balances, and perform unauthorized transactions.
Rebranded as Escobar
Using KELA‘s cyber-intelligence DARKBEAST platform, BleepingComputer found a forum post on a Russian-speaking hacking forum from February 2022 where the Aberebot developer promotes their new version under the name ‘Escobar Bot Android Banking Trojan.’
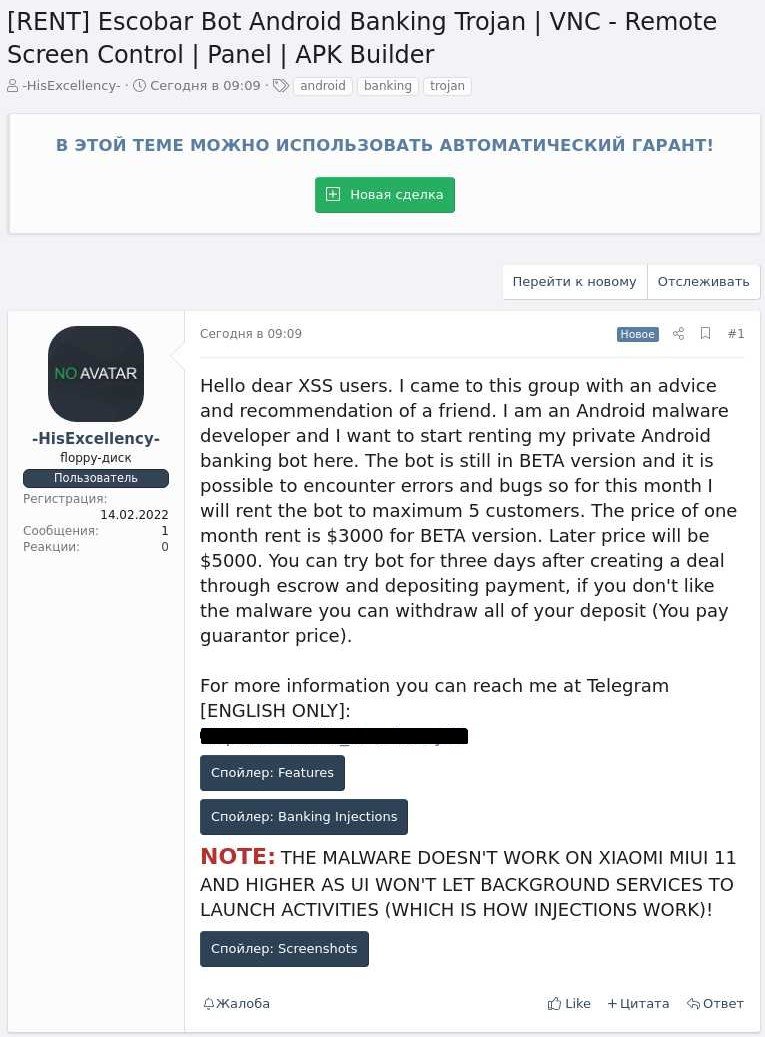
The malware author is renting the beta version of the malware for $3,000 per month to a maximum of five customers, with threat actors having the ability to test the bot for free for three days.
The threat actor plans on raising the malware’s price to $5,000 after development is finished.
MalwareHunterTeam first spotted the suspicious APK on March 3, 2022, masqueraded as a McAfee app, and warned about its stealthiness against the vast majority of anti-virus engines.
Possible interesting, very low detected “McAfee9412.apk”: a9d1561ed0d23a5473d68069337e2f8e7862f7b72b74251eb63ccc883ba9459f
From: https://cdn.discordapp[.]com/attachments/900818589068689461/948690034867986462/McAfee9412.apk
“com.escobar.pablo”
pic.twitter.com/QR89LV4jat— MalwareHunterTeam (@malwrhunterteam) March 3, 2022
This was picked up by researchers at Cyble, who performed an analysis of the new ‘Escobar’ variant of the Aberebot trojan.
According to the same analysts, Aberebot first appeared in the wild in the summer of 2021, so the appearance of a new version indicates active development.
Old and new capabilities
Like most banking trojans, Escobar displays overlay login forms to hijack user interactions with e-banking apps and websites and steal credentials from victims.
The malware also packs several other features that make it…


