AT&T Looks to Shut Down Botnet that Attacked 5,700 Network Appliances
AT&T is working to stop a botnet that has infected at least 5,700 network edge servers inside its networks and appears designed to steal sensitive information and launch distributed denial-of-service (DDoS) attacks.
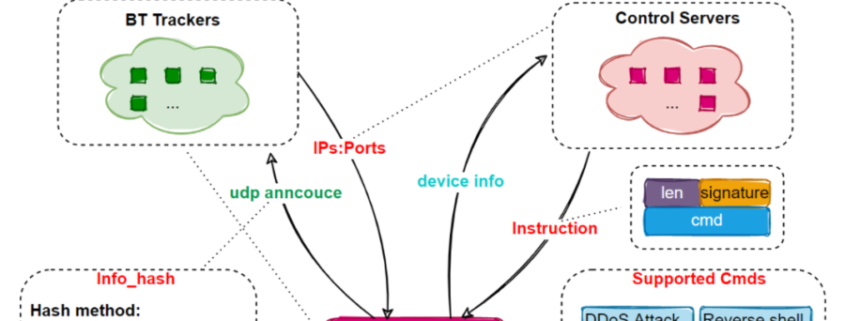
Researchers at Netlab, the network security unit of Chinese tech giant Qihoo 360, wrote in a report this week that the rapidly updated botnet was attacking voice-over-IP (VoIP) servers from Edgewater Networks that are housed within AT&T’s network and are designed to route traffic from enterprise customers to upstream mobile providers (in this case, AT&T).
The botnet was able to exploit an older vulnerability in unpatched EdgeMarc Enterprise Session Border Controllers (ESBCs) that is tracked as CVE-2017-6079. Once inside the appliances, the botnet installed a modular malware strain that the Netlab researchers dubbed EwDoor.
The researchers initially detected the botnet on Oct. 27, observing it attacking the ESBCs through the four-year-old vulnerability. They wrote that the botnet uses a “relatively unique” mount file system command in its payload.
A Short Window of Visibility
The initial version of EwDoor used a multiple command-and-control (C&C or C2) redundancy mechanism, but after having problems with the main C&C network, the botnet operators reconfigured the communication model and the researchers lost track of the botnet. However, during the short time they had sight of it, they confirmed that the targets were the Edgewater devices within the AT&T network and that all 5,700 appliances were located in the United States.
“So far, the EwDoor in our view has undergone 3 versions of updates, and its main functions can be summarized into 2 main categories of DDoS attacks and Backdoor,” they wrote. “Based on the attacked devices are telephone communication related, we presume that its main purpose is DDoS attacks, and gathering of sensitive information, such as call logs.”
The three updates occurred during November.
Also read: Top Vulnerability Management Tools for 2021
Exploiting the Edgewater Devices
According to the Netlab researchers, the botnet exploits a hidden page in the Edgewater appliances that includes user-defined commands. The bad actors can…