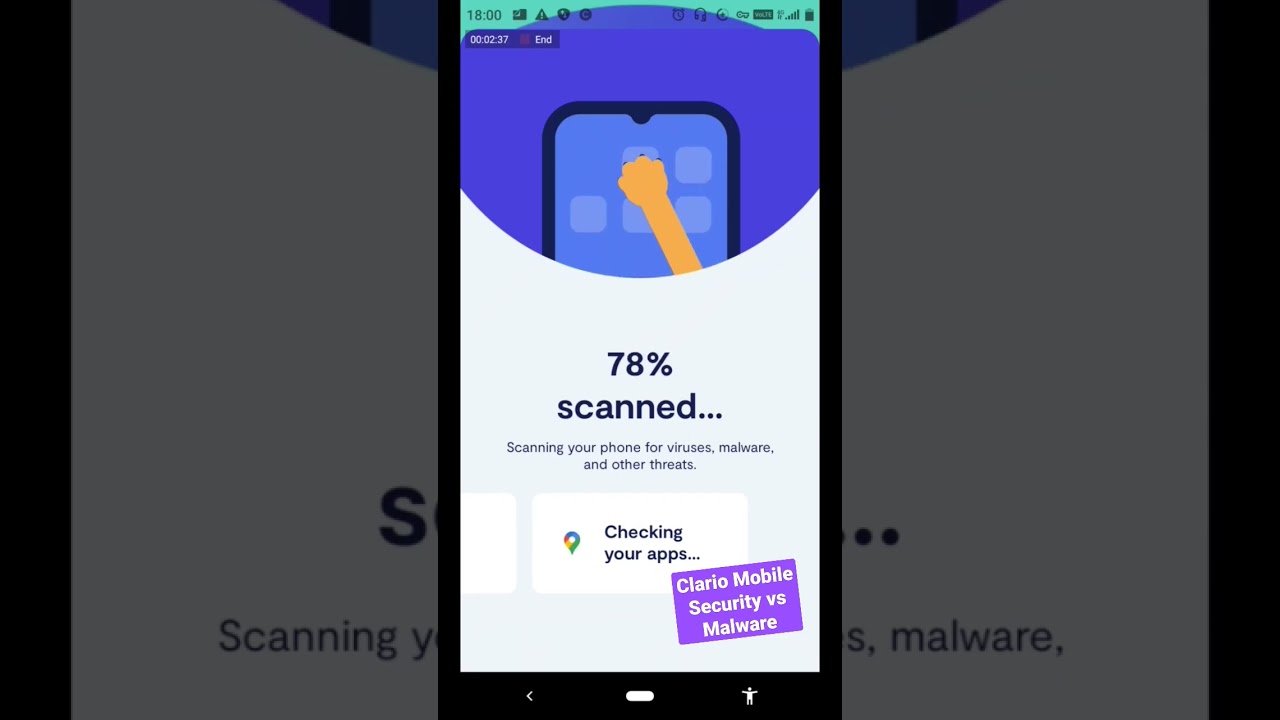
Azov Ransomware can modify its own code to delete every single file on a machine with a single click
A ransomware attack that is successful may be very detrimental to a company. In the event that an organization is caught unprepared, they may be forced to choose between paying a ransom demand or erasing all of the data that was taken. The WannaCry attack, which occurred more than 5 years ago, fundamentally altered cybersecurity. It was the first global-scaled, multi-vectored cyberattack in the form of an attack encrypting for and foremost, a compromised machine’s files, rendering it unusable, though reversible. Its outsized influence on the cyber threat landscape was outstanding, and it was an attack that encrypted for and foremost, a compromised machine’s files.
Since then, ransomware attacks have increased in number, form, and forms, and have evolved to use a variety of strategies and approaches.
The information security industry first became aware of Azov when it was discovered as a payload of the SmokeLoader botnet. This botnet is often located at fraudulent sites that provide unlicensed software and cracks.
The fact that Azov modifies some 64-bit executables in order to run its own code is one of the things that distinguishes it unique from the many other ransomware attacks that have been seen in recent years. The change of executables is accomplished via the use of polymorphic code in order to avoid the possibility of being blocked or discovered by static signatures. In addition, the modification is performed to 64-bit executables, which the typical malware programmer would not have bothered with.
According to the researchers at the Checkpoint “Because of this aggressive polymorphic infection of victim executables, there has been an increase in the number of Azov-infected files that are accessible to the public. VirusTotal receives hundreds of new Azov-related samples on a daily basis, and as of November 2022, the total number of these samples has already surpassed 17,000.”
Malware like Azov is one of a kind since it has the ability to develop its own code, making it simple for it to share personal information with other pieces of malware.
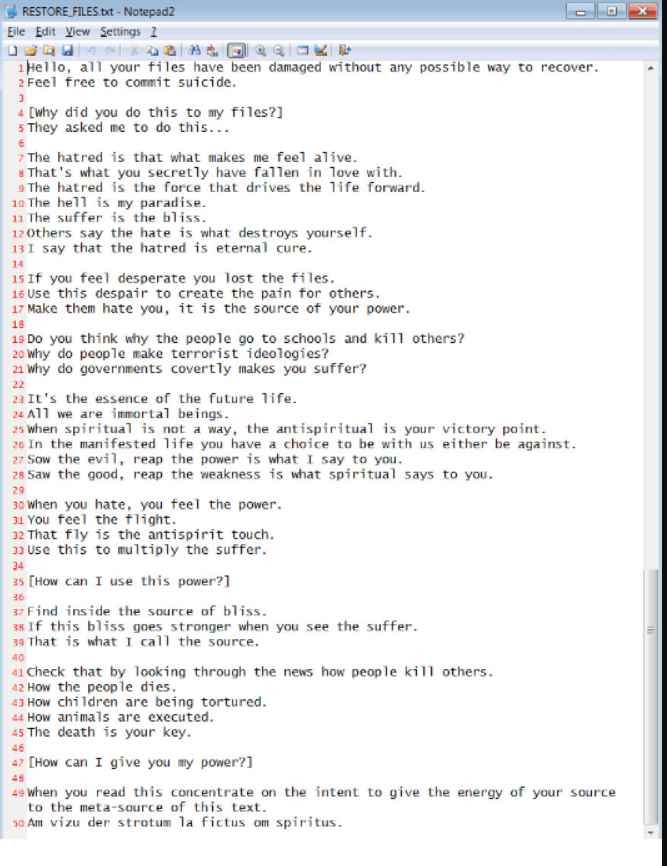
In addition to being able to write code, it also has the power of producing code, which allows it to…