Second Android 15 preview bolsters security to safeguard your files
What you need to know
- Further digging into Google’s second Android 15 preview shows increased security efforts to protect devices connected via USB.
- When attempting to switch USB modes, users will have to verify that it is them through various lock screen security methods.
- Google detailed its second Android 15 preview yesterday (Mar. 21), offering insight into its satellite connectivity and more.
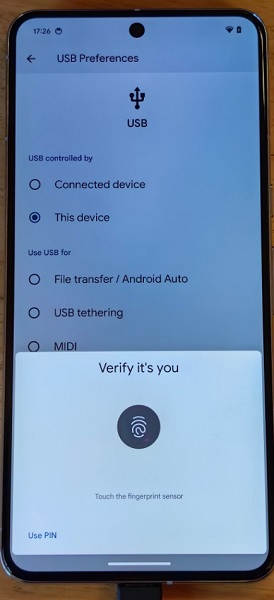
Google’s latest Android 15 preview gives users better insight into how it will protect your files when connected via USB.
According to Mishaal Rahman (Android Police), Android 15 Developer Preview 2 shows the software will require more “authentication” during USB-connected moments. To change which USB mode you’re in, Rahm discovered users must verify it’s truly them via lock screen measures such as their PIN, fingerprint, pattern, or password.
Such efforts will likely help give users peace of mind that nefarious actors can’t connect their devices to a computer and rip all of their sensitive data. However, Rahman notes that there is a slight security flaw with this within the developer preview.
He states that if “Developer Options” is left enabled, someone could still access your phone’s saved contents through “USB debugging.” This would virtually “verify” them, enabling them to copy all of your content to another device.
Rahman suggests that users should leave their device’s Developer Options disabled as a precaution until Google rectifies it.
In addition to transferring files, Android 15 DP2 requires users to authenticate the USB mode switch if swapping to Webcam, MIDI, PTP, and USB tethering.
Google revealed its second Android 15 preview yesterday (Mar. 21), and with it came another gaze into its satellite connectivity. The company is preparing to bring satellite connectivity for text messages and calls. Regarding the former, the preview showed Google’s support for SMS/MMS and RCS apps to send and receive messages.
Another aspect of the preview involved upgrading the NFC experience for users, making Android’s tap-to-pay feature smoother and more reliable. Android 15 was also seen…




