Cross-platform ElectroRAT malware drains cryptocurrency wallets

Security researchers have discovered a new remote access trojan (RAT) used to empty the cryptocurrency wallets of thousands of Windows, Linux, and macOS users.
Named ElectroRAT after being discovered in December, the cross-platform RAT malware is written in Golang and it was used as part of a campaign that has been targeting cryptocurrency users since the start of 2020.
Thousands infected within a year
The attackers behind the ElectroRAT operation created and injected their RAT into custom Electron applications made to look and behave like cryptocurrency trade management tools (Jamm and eTrade) and as a cryptocurrency poker app (DaoPoker).
After being launched on a victim’s computer, these apps would show a foreground user interface designed to divert the victims’ attention from the malicious ElectroRAT background process.
To lure potential victims, the threat actors promoted the trojanized apps on social media (Twitter and Telegram) and on dedicated online forums (bitcointalk and SteemCoinPan) according to an Intezer report shared with BleepingComputer earlier this week.
The malicious apps were downloaded by thousands of victims between January and December 2020, with one of the pastebin pages used by the malware to retrieve command-and-control (C2) server addresses having been accessed almost 6,500 times throughout the year.
“The trojanized application and the ElectroRAT binaries are either low detected or completely undetected in VirusTotal at the time of this writing,” Intezer says.
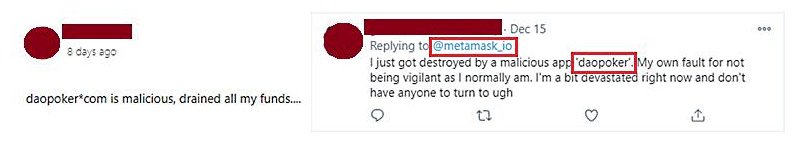
After getting infected and having their wallets drained by the malware’s operators, some of the victims were also seen warning others of the dangerous apps.
Switch from off-the-shelf to custom malware
C2 pastebin pages published by the same user who uploaded the ElectroRAT C2 info show that the attackers have also made use of off-the-shelf Amadey and KPOT information stealer trojans.
Both stealers target only the Windows platform and are well-known trojans that would make efforts to remain undetected almost impossible following infection.
The new Golang-based and undetected ElectorRAT malware was most likely a much more effective tool for a stealthy operation,…


