Defense in Depth to minimize the impact of ransomware attacks
Ransomware attacks continue to plague organizations globally regardless of their size. In a press release by the NCC group that preceded the Annual Threat Monitor Report 2021 published for the year 2021, there were an estimated 2,690 ransomware attacks, a 92.7% increase from 2020s figures of 1,389. The increase of ransomware attacks builds upon the general gradual rise in cyber-attacks in the wake of the COVID-19 pandemic. Ransomware accounted for roughly 65.4% of global cyber incidents in 2021. North America and Europe accounted for the most attacked regions with 53% and 30% of all the attacks respectively.
Ransomware Threat Trends
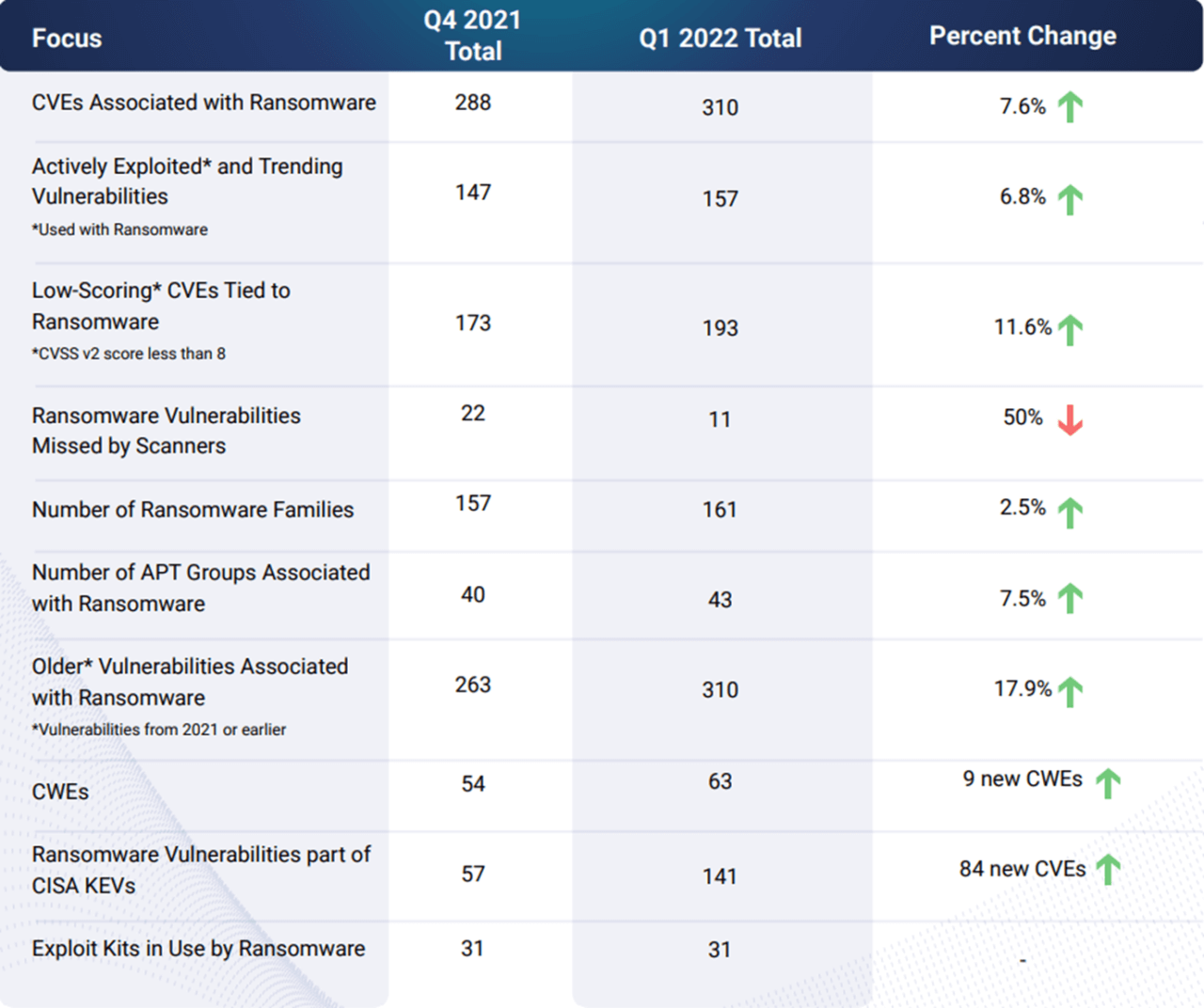
In a Ransomware report published by Cyber Security Works for Q1 of 2022, there has been an increase in eight of the ten ransomware foci. One positive revelation is that ransomware vulnerability detection capabilities appear to be improving. However, it is uncertain if this accounts for copycat variants, or if these are truly unique signature detections. Regardless of that curiosity, the figures in comparison to 2021 show the unrelenting nature of the current ransomware ecosystem.
Accordingly, in the PhishLabs Ransomware Playbook for Q1 2022, enterprises are specifically being targeted by ransomware operators to disable their critical systems and publish their stolen data. This has led to a 144% increase in ransom demands with victims being convinced more to pay ransoms in the hope their stolen data is not sold to third parties or published in criminal marketplaces.
Understandably, most organizations that suffer ransomware attacks are left with the options of either not paying and risking their data being exposed, or paying the ransom in the hope that the threat actor does not release their data afterwards. Either way, it is a difficult position to be in, one often influenced by (Read more…)


