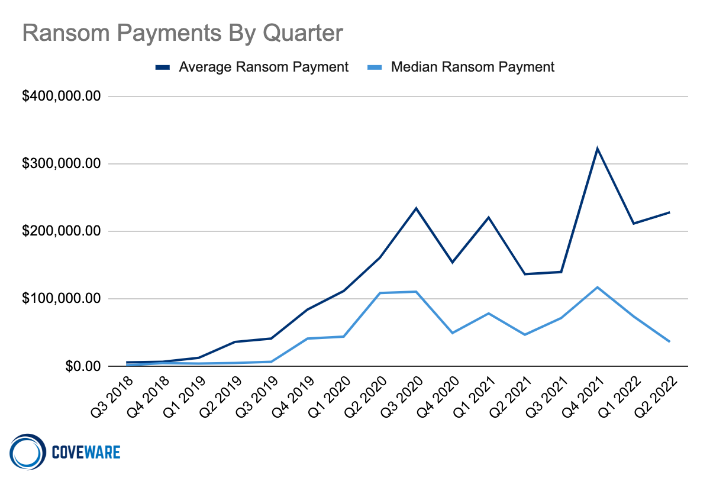
Fewer Ransomware Victims Pay, as Median Ransom Falls in Q2 2022
Table of Contents
Attack Vectors & MITRE ATT&CK Tactics
The cat and mouse game between ransomware affiliates and defenders spilled into new arenas of combat in Q2 of 2022. The looming question “What will happen once Conti disappears?” was answered rather quickly; nothing really changed except for name plates. The diaspora of Conti affiliates that was precipitated the Conti Leaks / Russian – Ukrainian invasion, were absorbed by existing and new Ransomware-as-a-Service (RaaS) groups such as Black Basta, BlackCat, Hive and Quantum.
Innovations in preventative policy evolved as two US States (Florida and North Carolina) banned municipal organizations from paying ransoms. Arguments from both sides of the debate weighed in, but the reality is that this is a worthy experiment and the data should be tracked very closely. The lack of uniform Blue Sky reporting may complicate analysis of if this policy is working vs. states that do not have similar laws.
However, The Cyber Incident Reporting Act, which provides mandatory incident reporting (a key element to data aggregation), was signed into law. The rule making and implementation time period means it may be 2+ years before the first report is filed with CISA. Expediting mandatory incident reporting would enable defenders to stay ahead of relentless cyber criminal innovation. Ransomware threat actors have been innovating as well. A year ago, a minority of ransomware variants were capable of encrypting non-Windows based operating systems. Today, almost ALL RaaS variants have stable Windows, Linux and ESXI versions and target every server, regardless of operating system.
Following the anniversaries of the Colonial pipeline and Kaseya attacks, defenders at large enterprises have had the opportunity to heavily invest in perimeter defense, privileged access management tools, segmentation, and continuity assets / strategies. These high profile attacks have enabled companies with ample security budgets and the right culture to make themselves very expensive targets for financially motivated attackers.
Ransomware affiliates seem to have become more…