First look at Portmaster, an open source cross-platform network monitor
Portmaster is a free open source cross-platform network activity monitor that is available in an early version for Windows and the Linux distributions Ubuntu and Fedora.
Portmaster combines traditional network activity monitoring with additional features, such as the option to enforce the use of secure DNS or the automatic blocking of advertisement, trackers and malicious hosts using filter lists, which are commonly used by ad-blockers.
Portmaster is free to use, which usually leads to the question of how development is financed. The developers behind Portmaster reveal information on that on the official project website. Basically, what they plan to do is use a freemium model. Portmaster will be free for all users but extra services, a VPN is mentioned specifically, is available for users who sign-up for it. Money is earned through that, which is used to finance development.
Portmaster: first look
An alpha version of Portmaster is available for Windows and Linux. It is released for testing and development purposes at the time. Alpha software may include bugs and issues, and should not be installed on production machines.
The development team notes that the alpha tag is “more about missing features than instability” of the application. Planned features for the first beta release include importing and exporting options, support for custom filter lists, cryptographically signed updates, and a full-device network monitor.
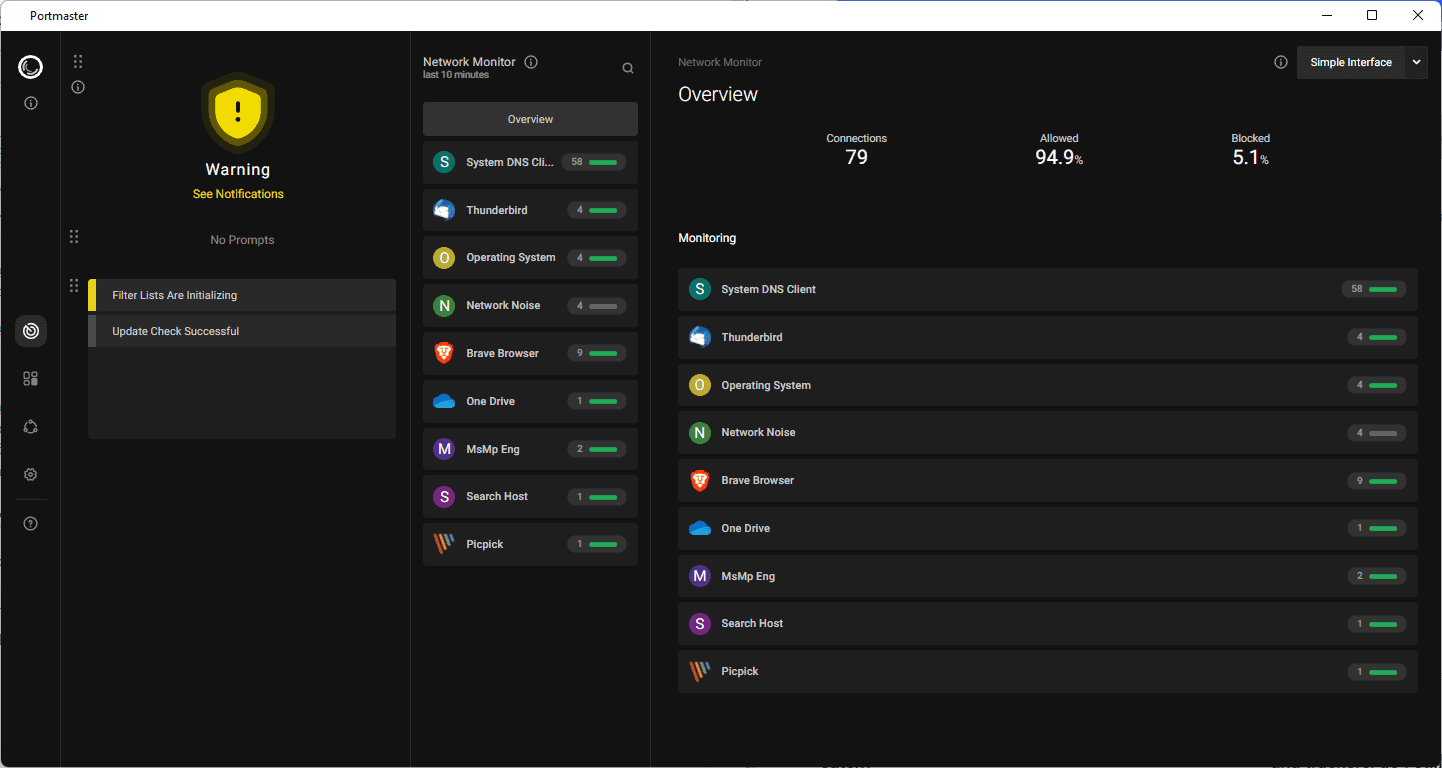
Installation is straightforward on Windows; a reboot is required to complete the installation process. The interface is well-designed and modern. The main page lists recent network activity, including the total number of connections, and the percentage of allowed and blocked connections.
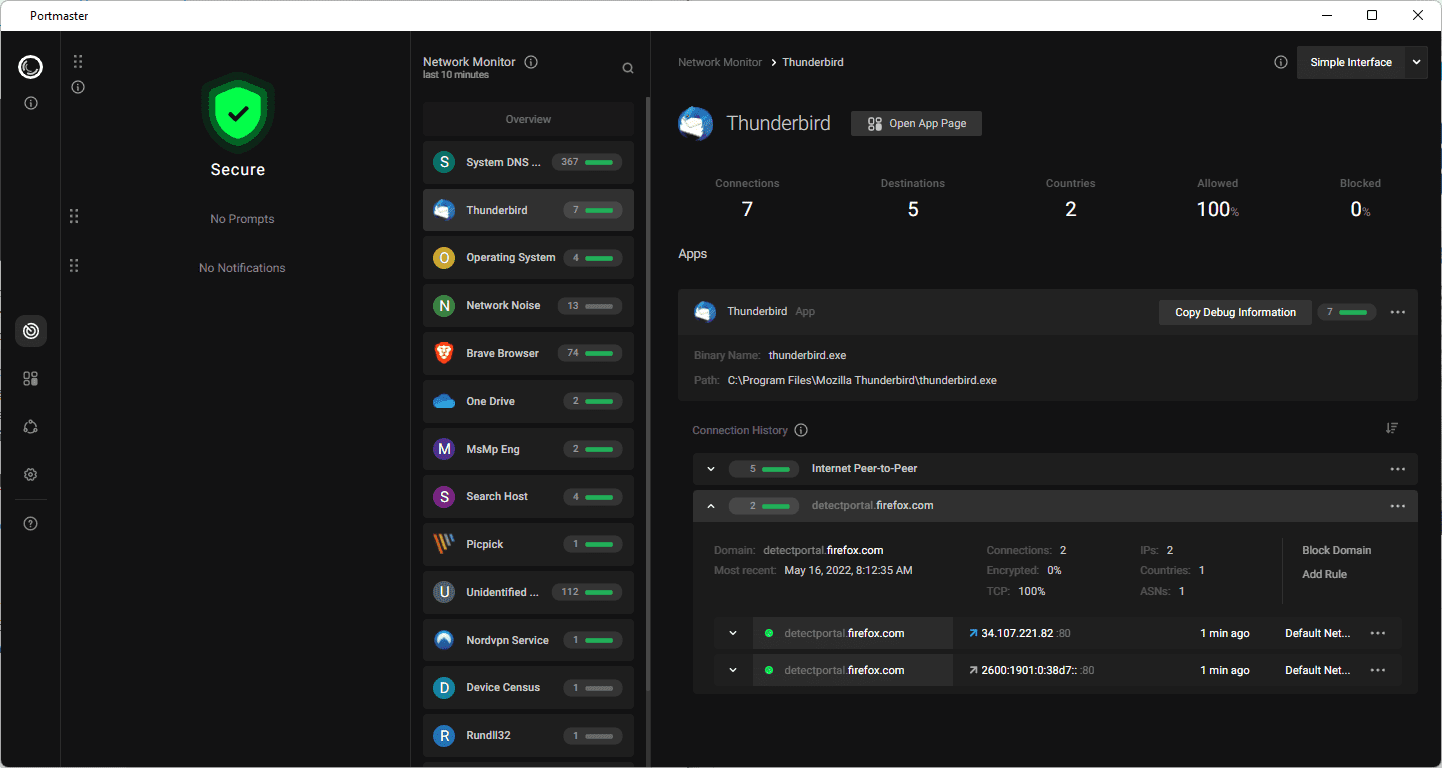
A click on an application or service in the network activity listing displays details, including name and path, and information about each connection that was made in the past.
Each connection is listed with the target, whether the data was encrypted, the IP addresses and countries of the IP addresses.
Settings can be defined for each individual application. Besides blocking all network activity, users may modify several connection specific options. To name a few:
- Switch…


