Google Finds New Exploit That Alters Chip Memory
Cybercrime
,
Endpoint Security
,
Fraud Management & Cybercrime
Latest Rowhammer Technique Targets Design Flaws in Modern DRAM Chips
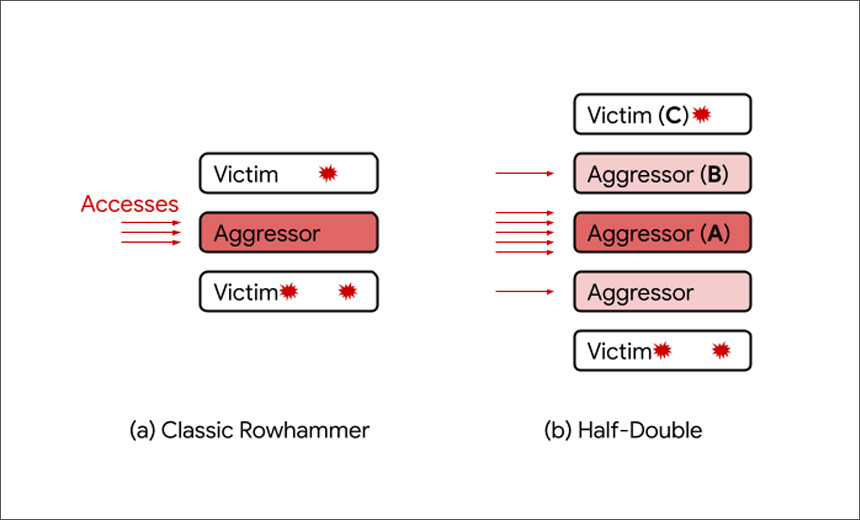
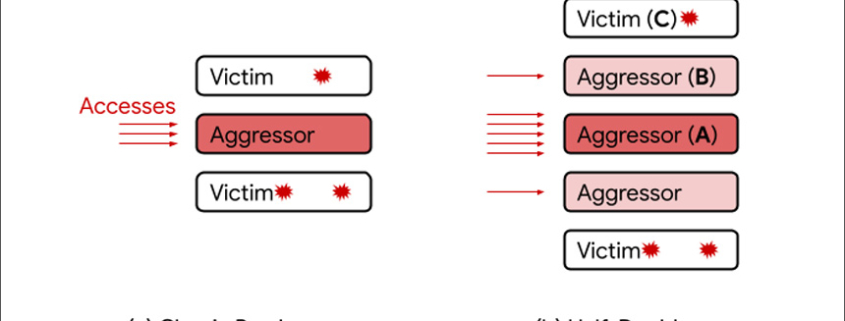
Researchers at Google have identified a new Rowhammer technique, dubbed Half-Double, which exploits design flaws in modern DRAM chips to alter their memory content.
See Also: Live Webinar | The Role of Passwords in the Hybrid Workforce
First discovered in 2014, Rowhammer is a DRAM vulnerability in which repeated access to one address can tamper with data stored in other addresses.
“Much like speculative execution vulnerabilities in CPUs, Rowhammer is a breach of security guarantees made by the underlying hardware. As an electrical coupling phenomenon within the silicon itself, Rowhammer allows the potential bypass of hardware and software memory protection policies. This can allow untrusted code to break out of its sandbox and take full control of the system,” the researchers at Google note.
The 2014 paper, however, discusses the DDR3, the mainstream DRAM generation at the time. In 2015, the Mountain View, California-based company’s Project Zero, which was tasked with finding zero-day vulnerabilities, released an exploit that escalates working privilege.
In response to the exploit, chip manufacturers implemented proprietary logic in their products that attempted to track frequently accessed addresses and reactively mitigate when necessary.
2014 saw the release of DDR4, which included built-in defense mechanisms, seemingly marking the end of Rowhammer.
In 2020, however, a paper on TRRespass…