Hacking group’s new malware abuses Google and Facebook services

Molerats cyberespionage group has been using in recent spear-phishing campaigns fresh malware that relies on Dropbox, Google Drive, and Facebook for command and control communication and to store stolen data.
The hackers have been active since at least 2012 and are considered to be the low-budget division of a larger group called the Gaza Cybergang.
Two backdoors and a downloader
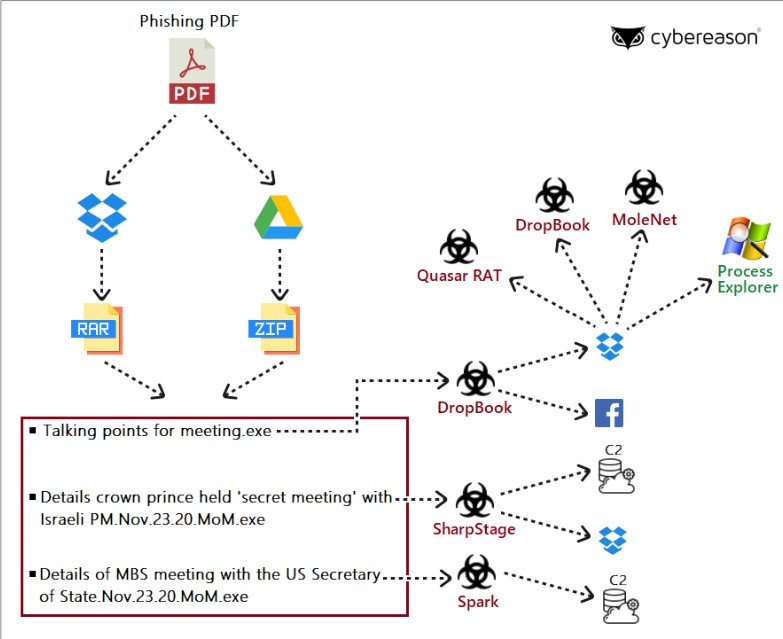
The Molerats threat actor used in recent operations two new backdoors – called SharpStage and DropBook, and one previously undocumented malware downloader named MoleNet.
Designed for cyberespionage, the malware attempts to avoid detection and takedown efforts by using Dropbox and Facebook services to steal data and receive instructions from the operators. Both backdoors implement Dropbox to extract stolen data.
The attack starts with an email luring political figures or government officials in the Middle East (Palestinian Territories, UAE, Egypt, Turkey) to download malicious documents.
One of the lures in campaigns delivering the new malware was a PDF file referencing the recent talks between Israeli Prime Minister Benjamin Netanyahu and His Royal Highness Mohammed bin Salman, Saudi Crown Prince.
The document showed only a summary of the content and instructed the recipient to download password-protected archives stored in Dropbox or Google Drive for the full information.
Two of these files were SharpStage and DropBook backdoors, which called a Dropbox storage controlled by the attacker to download other malware. A third one was another backdoor, Spark, also used by Molerats in previous campaigns.
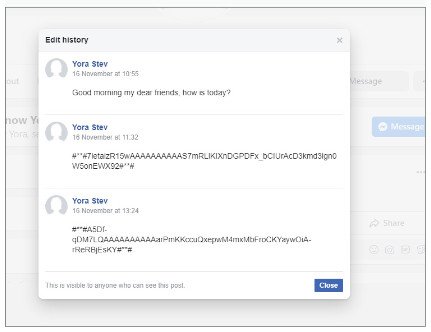
Commands over Facebook
A technical report from Cybereason’s Nocturnus Team [PDF] notes that the Python-based DropBook backdoor distinguishes from other tools in Molerats’ arsenal because it receives instructions only through fake accounts on Facebook and Simplenote, the note-taking app for iOS.
The hackers control the backdoor through commands published in a post on Facebook. They used the same method to provide the token necessary to connect to the Dropbox account. Simplenote acts as a backup in case the malware cannot retrieve the token from Facebook.
With commands coming from multiple sources on a…


