Hacking the World – Part 1: Hacking Basics

Each week in October, as part of Cybersecurity Awareness Month, we’ll publish an article packed with facts and stats, to give you an in-depth look at the state of cybersecurity in today’s world. We’ll start with the basics, then cover vulnerabilities, risks, costs – and so much more.
Cybersecurity is in focus now more than ever before – and 2020 was a record year for hacking activity. Companies faced swathes of sophisticated attacks during the initial throes of the COVID-19 pandemic and this trend has continued into 2021.
We’ll tell you everything you need to know about the scale, cost, and geography of hacking attacks and data breaches, not to mention stats on the biggest threats, vulnerabilities, and risk areas over the last 12 months.
We’ll even cover the future of cybersecurity and some tips to stay safe. But first, let’s take a look at the key definitions. Jump to a section below, or read on:
Cybersecurity Glossary
General Statistics
Hacking 101
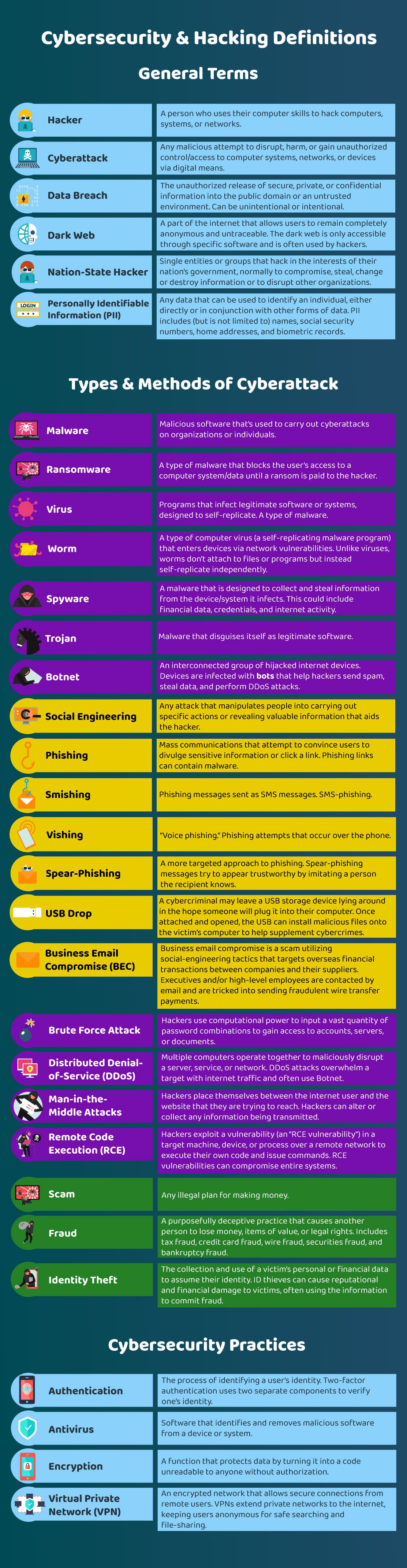
Cybersecurity Glossary
Digital rights refer to those rights that allow individua
Cybersecurity is a complicated subject with its fair share of technical jargon. Before we get into our long list of cybersecurity/hacking stats, let us first go over some key definitions.
This should help us avoid any confusion.
As you probably already know, cybersecurity is the protection of device users/contents against unauthorized electronic data and bad actors. Cybersecurity also outlines the measures taken to achieve this protection.
Hacking is the process of gaining unauthorized access to a system or device’s data. There are a ton of other cybersecurity and hacking-related definitions. Here are some important ones.
Now we’ll dive into the world of hacking and cybersecurity statistics…
General Statistics
Here are a few general stats to get you acquainted with cybersecurity and hacking: History, target data, and the current state of hacking breaches.
The History of Hacking

Hacking is almost as old as the very first computer network. That’s right, as long as computers have been around, people have been busy trying to figure out how best to exploit them.
Bob Thomas of BBM wrote the creeper — an experimental program…


