How to Prevent API Abuse

API abuse, when the API is used in an unexpected way, is a growing problem in software development and one of the leading attack vectors cybercriminals exploit. According to a recent security research report that surveyed more than 200 enterprise security professionals, there was a 21.32% growth in malicious API call volume between December 2020 and December 2021. The same study also established that 95% of respondents had suffered an API security incident in the past year.
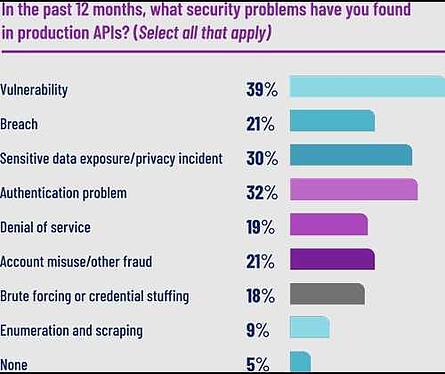
Source: Salt Security
Examples of API Abuse
Some typical examples of ways that APIs are abused include:
- Man in the Middle attacks: Attackers can use Man in the Middle (MitM) attacks to intercept communications between the app and the backend server. Once communications are intercepted, valuable or sensitive information may be seized and/or manipulated in order to use gain access to backend servers via the API.
- Repackaged or modified apps: Hackers can modify an existing app to include malicious code. The modified app then makes calls to the API to allow the attacker to access sensitive data or to convince genuine users to use the compromised app.
- Scripts or bots: Criminals can use scripts or bots to automate requests to the API in order to scrape data, apply compromised credentials, or overload the system. This is the most common form of API abuse and can lead to denial of service conditions among other conditions which will impact legitimate API users.
- Reverse engineered apps: Attackers can reverse engineer an app to discover the secrets it uses to access its API and the business logic contained within the app. The bad actor can then use this knowledge to make unauthorized calls to the API.
Why is API Abuse a Serious Issue?
Some of the reasons that API abuse is a major threat for organizations include:
- Lack of Awareness: One of the biggest challenges in preventing API abuse is that many organizations are simply unaware that it’s a problem. They may not have experienced an attack yet or may not be monitoring with sufficient granularity to detect this kind of suspicious activity. Specifically, many organizations lack the means to differentiate between a genuine user and a script/bot.
- Mobile Apps…



