Integrated Security for Telco Cloud Edge and Private 5G
Telcos and enterprises are realizing the need to move toward the edge and deploy edge cloud solutions to leverage the massive advances in transmission offered by 5G. Benefits such as speed, low-latency, capacity will drive major transformation for telcos and enterprises opening new revenue opportunities and business models.
Telcos and enterprises are exploring new use cases by deploying edge clouds and bringing content and applications closer to the users and billions of IoT devices to meet the low-latency requirements. The Ericsson 2022 mobility report forecasts that over 30 billion Internet of Things (IoT) connected devices will be connected by 2027.
The 5G core network functions could be deployed as a microservice in a private data center of the CSP and enterprise network or a public cloud, the shift to the edge and deploying telco cloud edge services and enterprise hybrid private 5G networks introduce new security threats that are associated with the 5G and edge deployment.
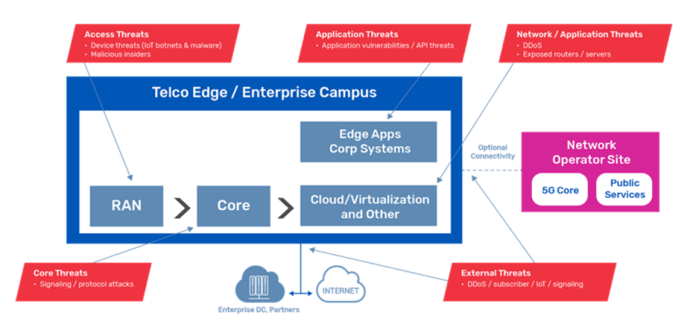
Even though there are security risks with 3G/4G, these risks are mainly associated with external attacks. However, with 5G/MEC/IoT architecture, this risk becomes larger and more serious. 5G core and edge sites can be attacked from the internal network in an “inside-to-outside” approach. Considering that 5G provides high-speed internet broadband, connecting a massive number of consumer and IoT devices, it can be considered as a new point of attack for the 5G cloud edge architecture.
Such massive transformation is forcing telcos and enterprises deploying cloud edge and private 5G services to re-think their security and network protection. There are many challenges in how telcos and enterprises deploy security solutions today as they cannot provide integrated 5G core and security solutions to adapt with cloud-edge use cases. For example, moving to the edge will require a low footprint, automation, scaling and simplified lifecycle management (LCM). Given the increase in the number of edge sites that may be deployed, it will be very complex to manually manage and scale different security solutions. The typical deployments of…

