Microsoft reveals details about how it discovered a security flaw in macOS Gatekeeper
Microsoft has revealed how it discovered a security flaw in macOS Gatekeeper. The vulnerability has been termed as Achilles.
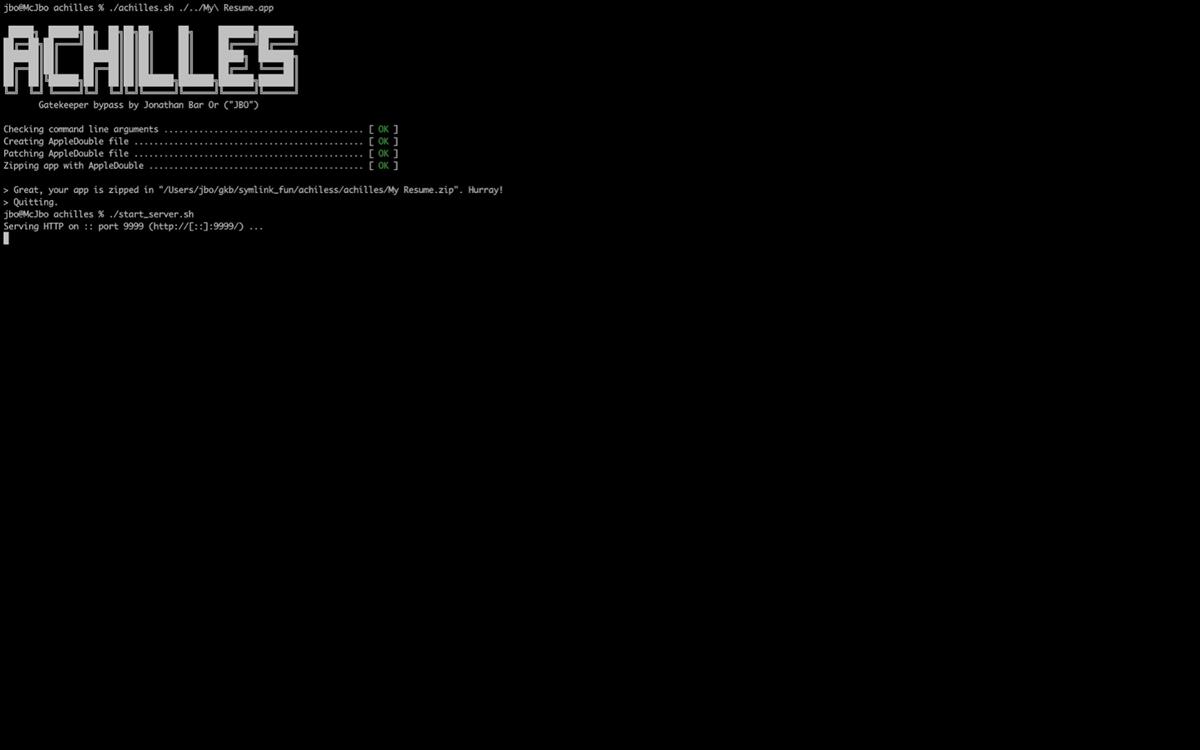
For those unaware, Gatekeeper is a security feature that protects your Mac, it does so by only allowing trusted software to run on it, it’s sort of like an antivirus. The security issue has been referenced as CVE-2022-42821. It has a severity rating of 5.5, which means it is a medium level threat.
Microsoft says that it analyzed the threat, and shared its findings with Apple in July through Microsoft Security Vulnerability Research, in order to help protect macOS users from potential attacks.
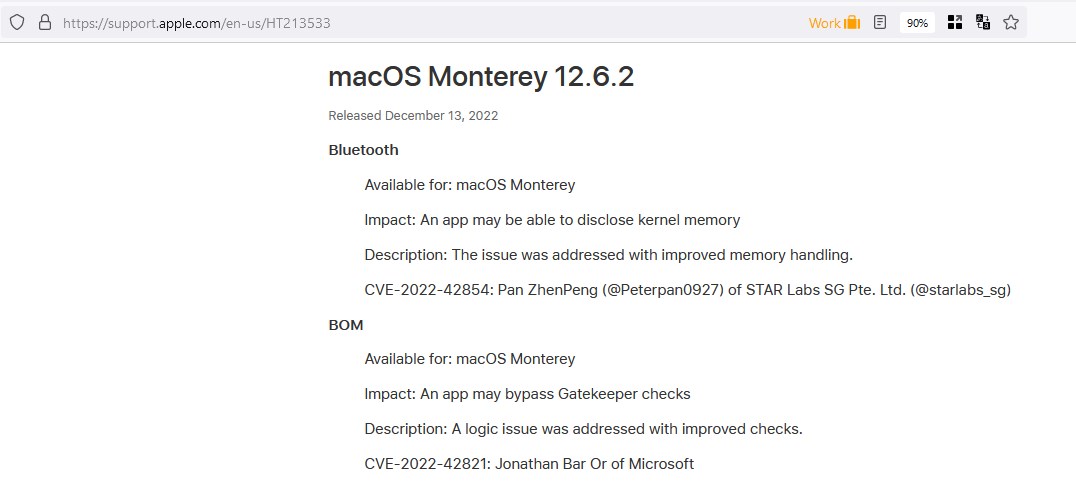
Apple patched the Achilles heel security flaw in macOS Ventura that was released on October 24th, and later in macOS Monterey 12.6.2 and macOS Big Sur 11.7.2, which were rolled out on December 13th. In its security notes, the Cupertino company had mentioned that the vulnerability could allow an app to bypass Gatekeeper checks, and that it a logic issue had been addressed with improved checks.
How Microsoft discovered the Achilles vulnerability in macOS
That doesn’t explain much, but an article on Microsoft’s security blog goes into the details. It is a bit on the technical side, so I’ll try to simplify it here. Microsoft says that macOS devices usually get infected as a result of users running fake apps that they may have downloaded from third-party sources, i.e. outside the App Store.
When a user downloads a file through their web browser, macOS assigns an extended attribute to it called com.apple.quarantine. The browser saves the metadata of a downloaded file in the above-mentioned attribute, and it contains some information such as flag;date;agent_name;UUID.
This is used by Gatekeeper to enforce some security policies. macOS usually warns you when you are trying to install something downloaded from the internet, that’s because Gatekeeper read its extended attribute, and recognized it as an app from an unknown source. After analyzing past security vulnerabilities that were present in macOS, Microsoft security researchers identified a specific one, referenced as CVE-2021-1810. The loophole, which was patched a year ago, would create a symbolic link to an app…


