Multi-Factor Authentication is Not Foolproof Protection
Multi-Factor Authentication (MFA) has become increasingly common both in business and personal use. Yet, despite MFA providing increased security, threat actors are using the availability of sophisticated technology and even legitimate infrastructure to bypass this and access corporate networks and personal data.
To the uninitiated, MFA is when a user is required to provide two or more verification factors. The most typical type of MFA employed is Two Factor Authentication (2FA), when a user signs on to a site with their username and password and receives a code sent to a secondary device such as a mobile phone, email, or authenticator app. Once this code is entered into the site, it grants access. Until now, this security has been reasonably effective, and therefore users feel assured that it is entirely tamper-proof if the attacker does not have access to the secondary device which receives the code.
However, the bad actors have found ways to bypass MFA, putting network security at risk.
Man-in-the-Middle or Web Proxy Attack
The first technique bad actors employ is a man-in-the-middle (MitM) or reverse web proxy attack. This is when an attacker sends the user a link either through email or SMS that directs them to a phishing website. The link leads the user to a fake replica of a legitimate site – one that is nearly impossible to recognize as not legitimate for the average user.
For example, assume a Chase bank login page employs 2FA (Example 1). The attacker knows that even if they get the username and password, they still cannot access the site. And so, they use a reverse Web proxy between the phishing page and the actual service i.e., the man-in-the-middle.
Once the user enters the credentials, the phishing page will ‘talk’ to the original service, which will send the user the token or code to enter. At this point, the phishing page gets the code because the user enters it assuming s/he is on the official site. This gives the attacker the username, password, and code to authenticate with the real service and compromise the account.
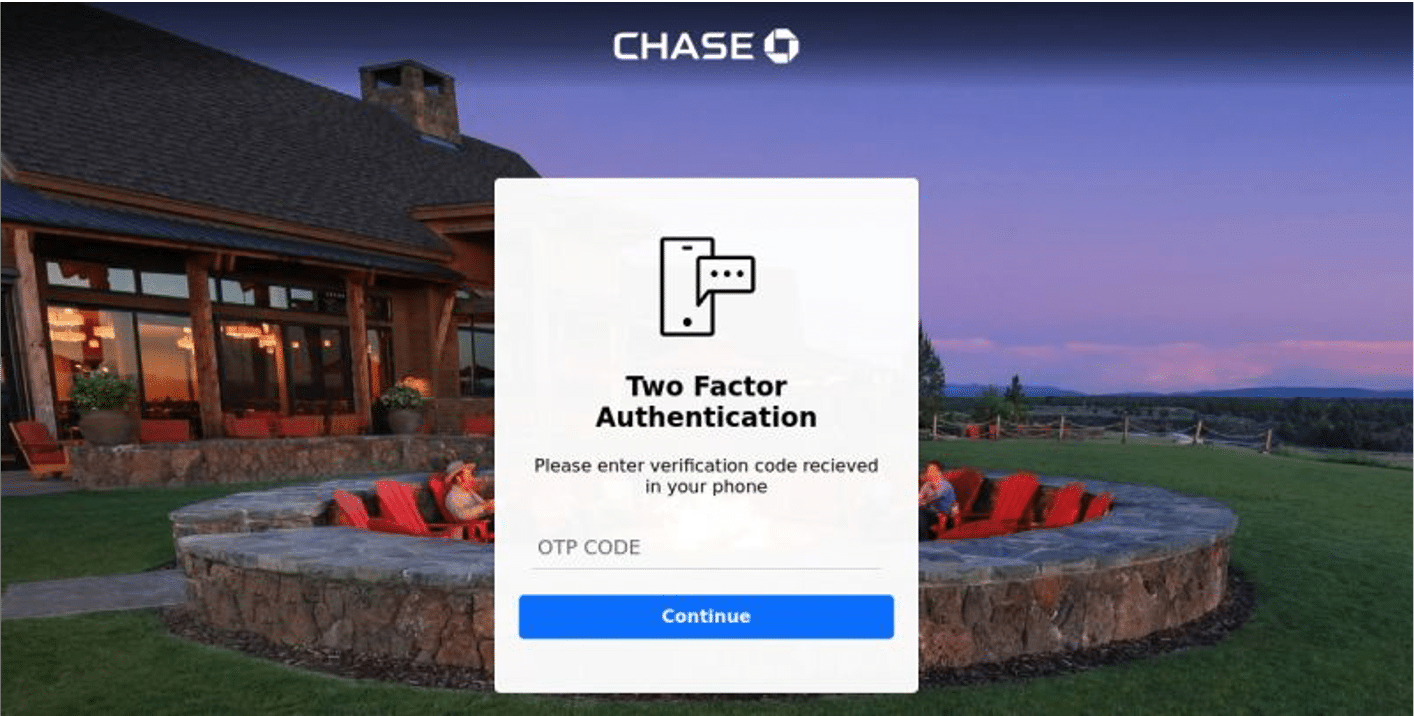
Example 1: A phishing site using reverse web proxy to hijack session cookies
Even more troubling, this type of attack is…


