New malware sample confirms gang is back
The notorious REvil ransomware operation has returned amidst rising tensions between Russia and the USA, with new infrastructure and a modified encryptor allowing for more targeted attacks.
In October, the REvil ransomware gang shut down after a law enforcement operation hijacked their Tor servers, followed by arrests of members by Russian law enforcement.
However, after the invasion of Ukraine, Russia stated that the US had withdrawn from the negotiation process regarding the REvil gang and closed communications channels.
REvil’s Tor sites come back to life
Soon after, the old REvil Tor infrastructure began operating again, but instead of showing the old websites, they redirected visitors to URLs for a new unnamed ransomware operation.
While these sites looked nothing like REvil’s previous websites, the fact that the old infrastructure was redirecting to the new sites indicated that REvil was likely operating again. Furthermore, these new sites contained a mix of new victims and data stolen during previous REvil attacks.
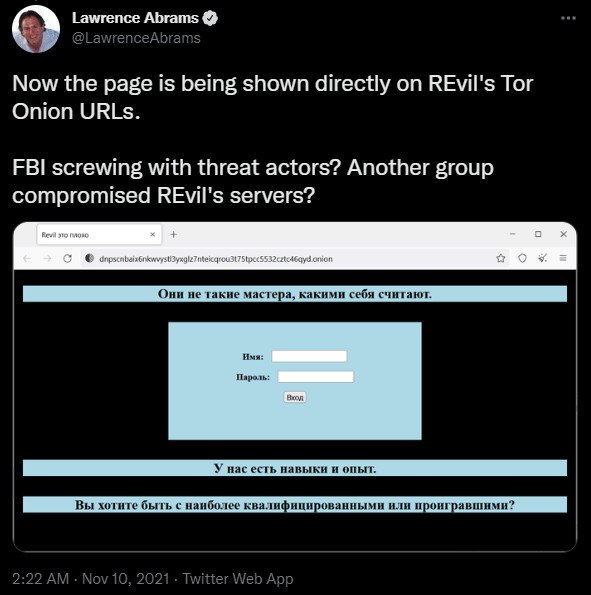
While these events strongly indicated that REvil rebranded as the new unnamed operation, the Tor sites had also previously displayed a message in November stating that “REvil is bad.”
This access to the Tor sites meant that other threat actors or law enforcement had access to REvil’s TOR sites, so the websites themselves were not strong enough proof of the gang’s return.
Source: BleepingComputer
The only way to know for sure whether REvil was back was to find a sample of the ransomware encryptor and analyze it to determine if it was patched or compiled from source code.
A sample of the new ransomware operation’s encryptor was finally discovered this week by AVAST research Jakub Kroustek and has confirmed the new operation’s ties to REvil.
Ransomware sample confirms return
While a few ransomware operations are using REvil’s encryptor, they all use patched executables rather than having direct access to the gang’s source code.
However, BleepingComputer has been told by multiple security researchers and malware analysts that the discovered REvil sample used by the new operation is compiled from…


