New Ransomware Attack Tries to Frame Security Researchers

Most ransomware tries to extract a ransom for the restoration of files, hence the name. Whether or not the nefarious individuals behind the attack hold up their side varies, but a new version of the Azov Ransomware doesn’t bother. Instead of demanding Bitcoin, it tells infected individuals to contact security researchers and cybersecurity publication BleepingComputer, as if they are the authors of the malware. However, this is just an attempt to frame the good guys.
While Azov has some features of ransomware, and it presents itself as such, it’s more accurate to call it a data wiper. The updated malware began appearing on systems over the past few days after purchasing installs via the SmokeLoader malware. People often pick up SmokeLoader on sketchy sites that offer key generators, software cracks, and game cheats. This botnet is used to distribute numerous pieces of nasty hacking software, including other ransomware. There are even people whose systems have been double-encrypted, first by Azov and then by the STOP ransomware.
When introduced on a system, the malware launches itself from a temporary directory, usually with the addition of a Windows registry key. The executable scans all drives on the computer to find files that don’t have ini, exe, or dll extensions. Whenever it finds something else, like a document, image, or video, it encrypts it and appends the .azov file extension to the end.
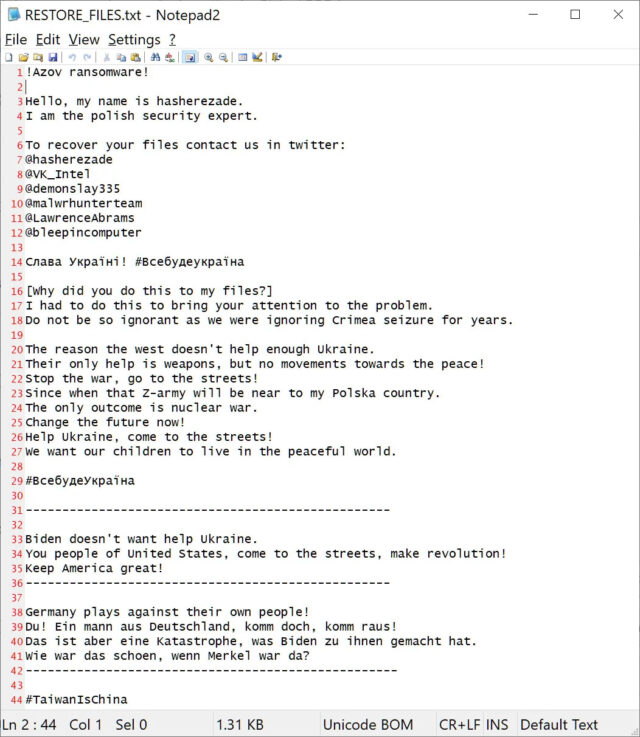
In each folder containing encrypted files, Azov creates a text document called “RESTORE_FILES.txt,” which you can see above. Usually, this is where your average ransomware would ask for money to decrypt the files. As BleepingComputer reports, the text document claims to be written by Polish security researcher and malware analyst Hasherezade. The document tells users to reach out to Hasherezade, BleepingComputer (and owner Lawrence Abrams), Vitali Kremez, and other cybersecurity pros on Twitter. Hasherezade notes in a statement that it’s common for malware authors to try and frame researchers.
Naturally, none of those people will be able to do anything about the encrypted files, but that’s…