Oh great: hackers are selling tools to hide malware in your GPU
If you thought your GPU was safe from malware then you’d be mistaken, according to a new report from Bleeding Computer, malware that can execute code from your GPU is now a reality.
VIEW GALLERY – 2 IMAGES
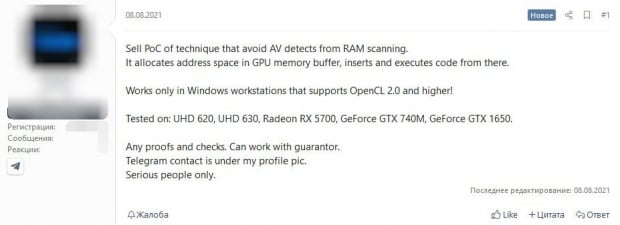
It seems that a proof-of-concept (PoC) was up for sale on a hacker forum and allows hackers to keep malicious code stored in your GPU memory buffer, which stops malware code from being scanned by security software when it scans the system RAM.
The seller of the GPU-focused malware says that it only works on Windows systems with support for version 2.0 and above of the OpenCL framework. This is required for executing the malware on the GPU, with the hacker testing it on Intel, AMD, and NVIDIA GPUs.
But is this GPU-focused malware in the wild? Yep.
On August 25 the seller said they sold the PoC without talking about the deal too much, just two weeks after posting about the PoC. Another member on the same hacker forum said that the GPU-based malware has worked before, with the Linux-based GPU rootkit called JellyFish… from 6 years ago.