Printer plays AC/DC, Samsung Galaxy S21 hacked twice

Trend Micro’s ZDI has awarded $1,081,250 for 61 zero-days exploited at Pwn2Own Austin 2021, with competitors successfully pwning the Samsung Galaxy S21 again and hacking an HP LaserJet printer to play AC/DC’s Thunderstruck on the contest’s third day.
Contestants earned $70,000 during the fourth day, $238,750 on the third day, $415,000 on the second, and $362,500 during the first day.
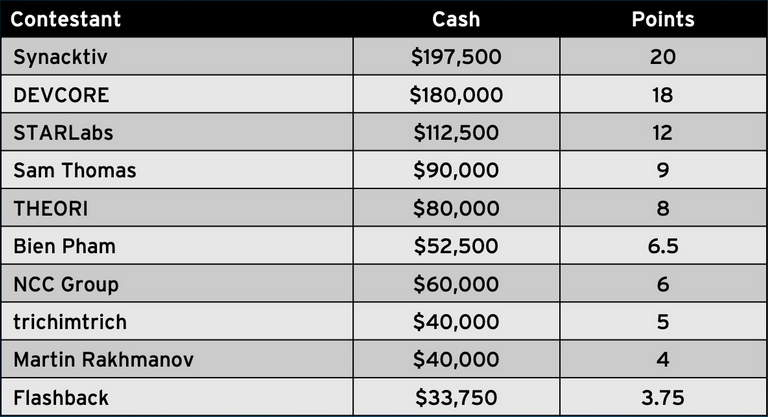
The Synacktiv team won the contest after getting $197,000 in cash for their zero-days and 20 Master of Pwn points, with a six-point lead over the DEVCORE team, which finished with 14 points and earned a total of $140,000.
Over the four days of competition, the contestants compromised printers, routers, NAS devices, and speakers from Canon, HP, Western Digital, Cisco, Sonos, TP-Link, and NETGEAR after exploiting 61 previously unknown security flaws known as zero-day vulnerabilities.
The full Pwn2Own Austin 2021 schedule and the results following each challenge are available here.
Sam Thomas (@_s_n_t) from team Pentest Limited (@pentestltd) was the one who compromised the Samsung Galaxy S21 running the latest Android 11 security updates on the third day using a unique three-bug chain and earning $50,000.
The Samsung Galaxy S21 escaped a hacking attempt on the first day after F-Secure Labs’ Ken Gannon didn’t get his zero-day exploit to work within the allotted time.
Mr L and Nguyễn Hoàng Thạch (@hi_im_d4rkn3ss) of STARLabs were able to get code execution on the Samsung Galaxy S21 on the second day of Pwn2Own.
However, despite their success and winning $25,000, their attempt was tagged as a “collision” after it was revealed that they used a bug known to the vendor.
The third day of Pwn2Own also saw the F-Secure Labs team turning an HP LaserJet printer into a jukebox using a stack-based buffer overflow to play AC/DC’s Thunderstruck.
(Sound On) Confirmed! The team from @FSecureLabs used a stack-based buffer overflow to take over an HP LaserJet and turn it into a jukebox. Their efforts earn them $20,000 and 2 Master of Pwn points. #Pwn2Own https://t.co/3kqn5Cr7Y4
— Zero Day Initiative (@thezdi) November 4, 2021
At this edition of…