Pro-Russia hack campaigns are running rampant in Ukraine

Getty Images
Pro-Russian threat actors are continuing their unrelenting pursuit of Ukrainian targets, with an array of campaigns that include fake Android apps, hack attacks exploiting critical vulnerabilities, and email phishing attacks that attempt to harvest login credentials, researchers from Google said.
One of the more recent campaigns came from Turla, a Russian-speaking advanced persistent threat actor that’s been active since at least 1997 and is among the most technically sophisticated in the world. According to Google, the group targeted pro-Ukrainian volunteers with Android apps that posed as launchpads for performing denial-of-service attacks against Russian websites.
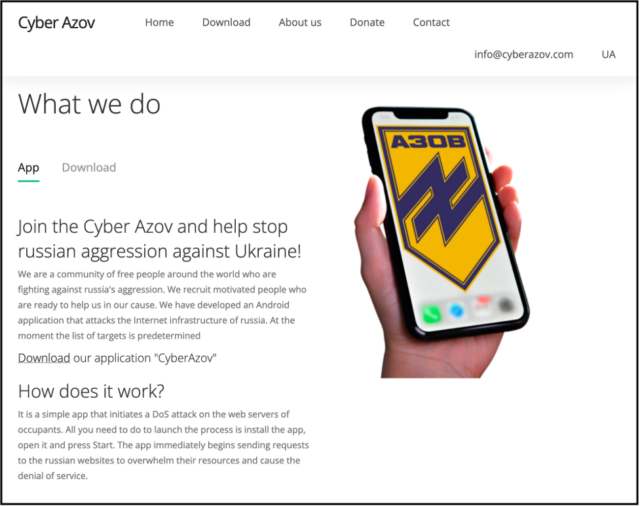
“All you need to do to launch the process is install the app, open it and press start,” the fake website promoting the app claimed. “The app immediately begins sending requests to the Russian websites to overwhelm their resources and cause the denial of service.”
In fact, a researcher with Google’s threat analysis group said, the app sends a single GET request to a target website. Behind the scenes, a different Google researcher told Vice that the app was designed to map out the user’s Internet infrastructure and “work out where the people that are potentially doing these sorts of attacks are.”
The apps, hosted on a domain spoofing the Ukrainian Azov Regiment, mimicked another Android app Google first saw in March that also claimed to perform DoS attacks against Russian sites. Unlike the Turla apps, stopwar.apk, as the latter app was named, sent a continuous stream of requests until the user stopped them.
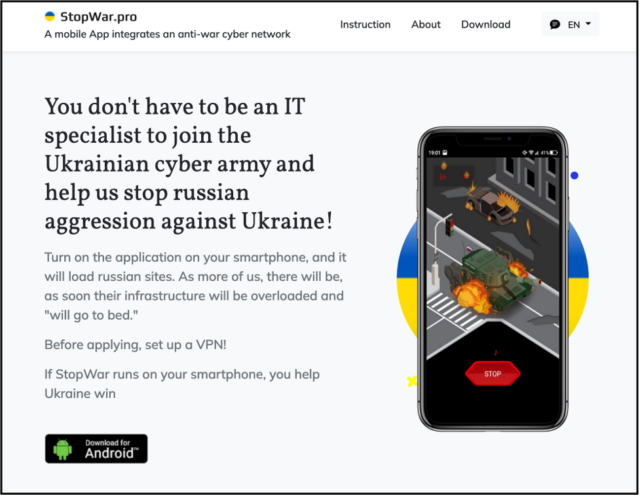
“Based on our analysis, we believe that the StopWar app was developed by pro-Ukrainian developers and was the inspiration for what Turla actors based their fake CyberAzov DoS app off of,” Google researcher Billy Leonard wrote.
Other hacking groups sponsored by the Kremlin have also targeted Ukrainian groups. Campaigns included the exploitation of Follina, the name given to a critical vulnerability in all supported versions of Windows that was actively targeted in the wild…


