QNAP investigating new Deadbolt ransomware campaign
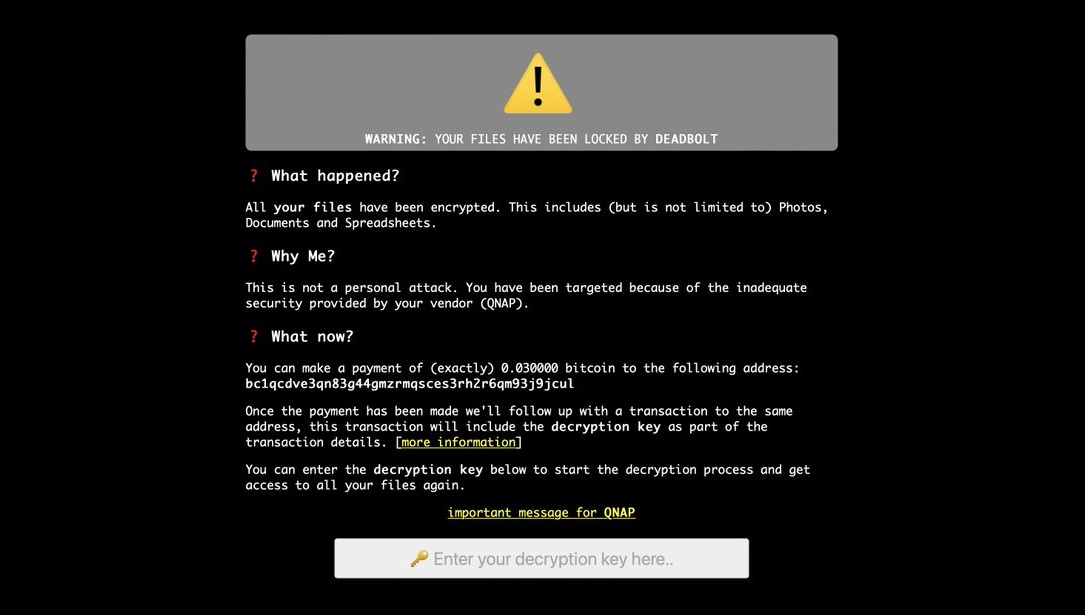
Taiwanese hardware vendor QNAP said on Friday that it is investigating yet another Deadbolt ransomware campaign targeting users of its network-attached storage (NAS) devices.
The company did not respond to requests for comment but released an advisory saying it recently detected a new batch of DeadBolt ransomware victims.
“According to victim reports so far, the campaign appears to target QNAP NAS devices running outdated versions of QTS 4.x. We are thoroughly investigating the case and will provide further information as soon as possible,” the company said.
QNAP urged customers to update their QTS or QuTS hero systems to the latest version as soon as possible.
For those who have already been compromised, QNAP said they should take a screenshot of the ransom note – in order to keep the Bitcoin address – then “upgrade to the latest firmware version.”
“The built-in Malware Remover application will automatically quarantine the ransom note which hijacks the login page,” QNAP explained.
“If you want to input a received decryption key and are unable to locate the ransom note after upgrading the firmware, please contact QNAP Support for assistance.”
Almost exactly one month ago, QNAP released a similar warning after several customers reported Deadbolt ransomware infections.
There continues to be significant debate among QNAP NAS users about whether even updated versions of the system are still vulnerable to the ransomware, which emerged in January. It is unclear where members of the Deadbolt ransomware group are based.
In January, dozens of people turned to QNAP message boards and Reddit to say they logged on only to find the Deadbolt ransomware screen. People reported losing decades of photos, videos and irreplaceable files.
Other companies’ devices also have been attacked. Users of Asustor’s NAS…