Sinkholing May Not Spell the End for Malware Hosts and Botnets
Sinkholing has long been employed as an effective cybersecurity solution to curb the spread of dangerous malware. Remember the infamous WannaCry ransomware outbreak in 2019? Security teams put a stop to the threat through sinkholing.
More recently, Microsoft sinkholed the web properties associated with Strontium, a Russian threat actor group that has been targeting Ukrainian sites via various cyber attacks.
While the tactic undoubtedly works, some trends related to ongoing threats may remain unknown. We hope to change that with this analysis conducted by WhoisXML API threat researcher Dancho Danchev, which gives cybersecurity teams more insights into sinkholed domains. The know-how can clue them into more web properties that may need to be taken offline as well.
Our in-depth analysis revealed:
- More than 13,000 malware and botnet hosts sinkholed recently
- A huge majority of the sinkholed domains appeared to be created using domain generation algorithms (DGAs)
- Most of the sinkholed domains used the .com top-level domain (TLD) extension
- A majority of the sinkholed domains existed for at least five years prior to being taken down
As part of our ongoing effort to enable cybersecurity analysts and researchers to further their studies, we collated the pertinent data and made it available to anyone interested. You may download Danchev’s report and related threat research materials here.
Analysis and Findings
We began our investigation by obtaining 24 email addresses that are known to have been used to sinkhole domains connected to ongoing malware and botnet operations.
Sinkholed Domains
Using these email addresses as reverse WHOIS search terms led to the discovery of 13,265 domains. Examples include:
- lztorsixnikxicahclbrasqu[.]org
- azslrhksyldb[.]org
- bqkrtxgkmriwsiwcngtivpx[.]info
- fkbpvfnbhfwedagussg[.]com
- honeybot[.]us
- quicklygood[.]gdn
- gramblr[.]ca
- empire-js[.]us
- eitherplunge[.]gdn
- ee0[.]us
The domain distribution per email address (which we partially redacted for privacy reasons) is shown below.
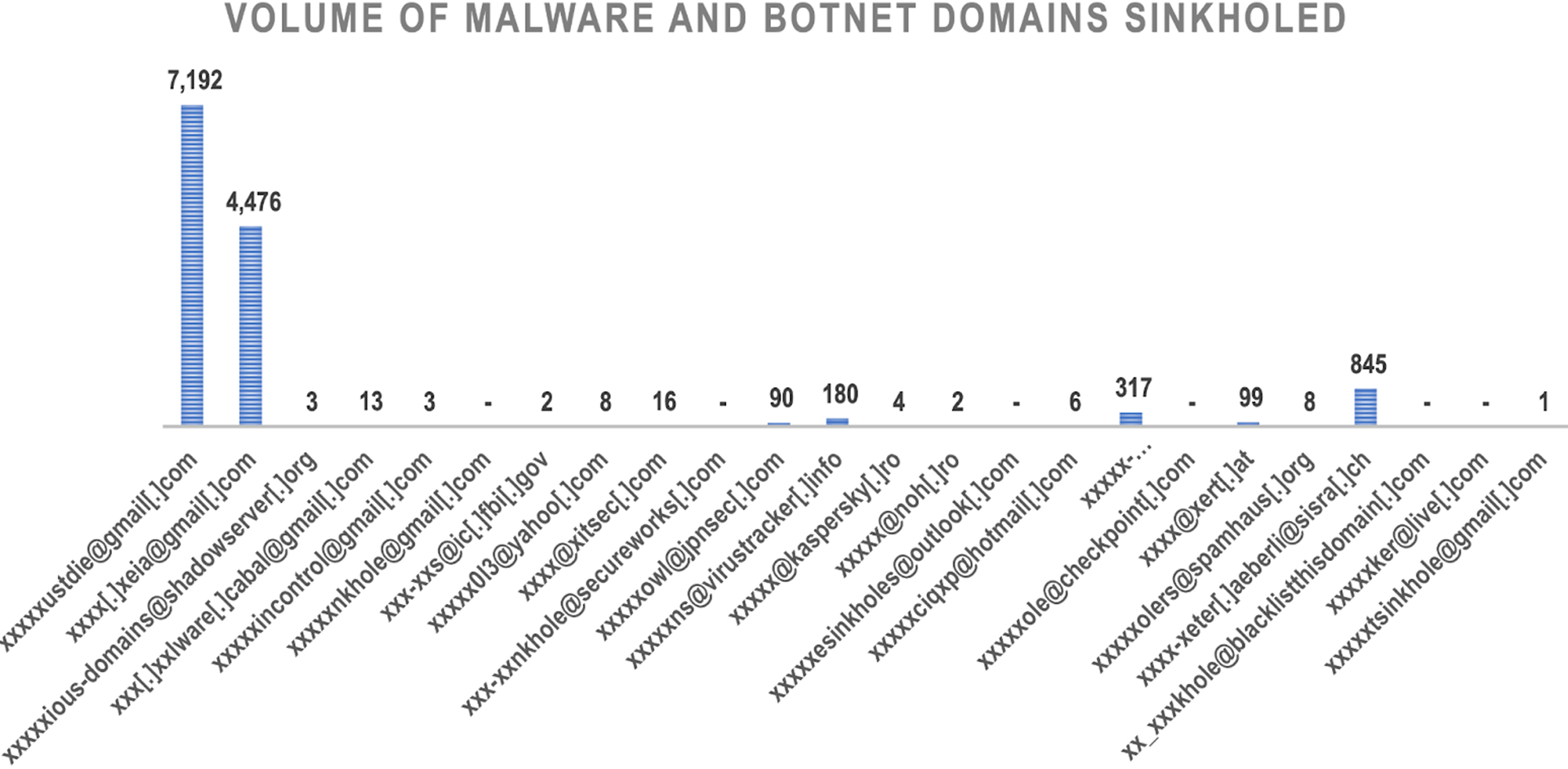
Several nonprofit organizations, big cybersecurity companies, and government agencies like the Shadowserver Foundation, the Federal Bureau of Investigation (FBI),…


