Supporting At-the-Edge Processing with CDN Integrations
DataDome’s mission is to protect our customers against threats on any infrastructure. In the past, companies would often use their own on-premise web and application servers to host important resources, or rely on their content delivery network (CDN) to provide bot detection. But today’s far-reaching internet requires far more distributed resources than most companies can sustain. Cloud computing and CDNs now meet that need, but the places they fall short in terms of cybersecurity are more impactful than ever.
- Security: Many CDNs include their own non-transferable security. However, it is not the best, most comprehensive security tool available, and most likely does not cover specific threats—especially sophisticated bot attacks—as well as you need.
- Updates: Because CDNs become part of your website infrastructure, they need to be bulletproof, or they could become vectors for attacks by malicious actors. CDNs may not update or patch as regularly as they should because that is not the primary focus of their business.
- Attacks: CDNs, which exist to serve internet resources across the globe, are just as likely to be attacked as specific websites, servers, and mobile apps. For instance, many CDNs face distributed denial of service (DDoS) attacks that attempt to overwhelm their resources to ultimately take down the target site—or every single site serviced by that CDN. DDoS attacks are easier than ever to perform thanks to proxy IP addresses and bots-as-a-service vendors, and if your CDN isn’t prepared to handle high-volume bot traffic, it may fail.
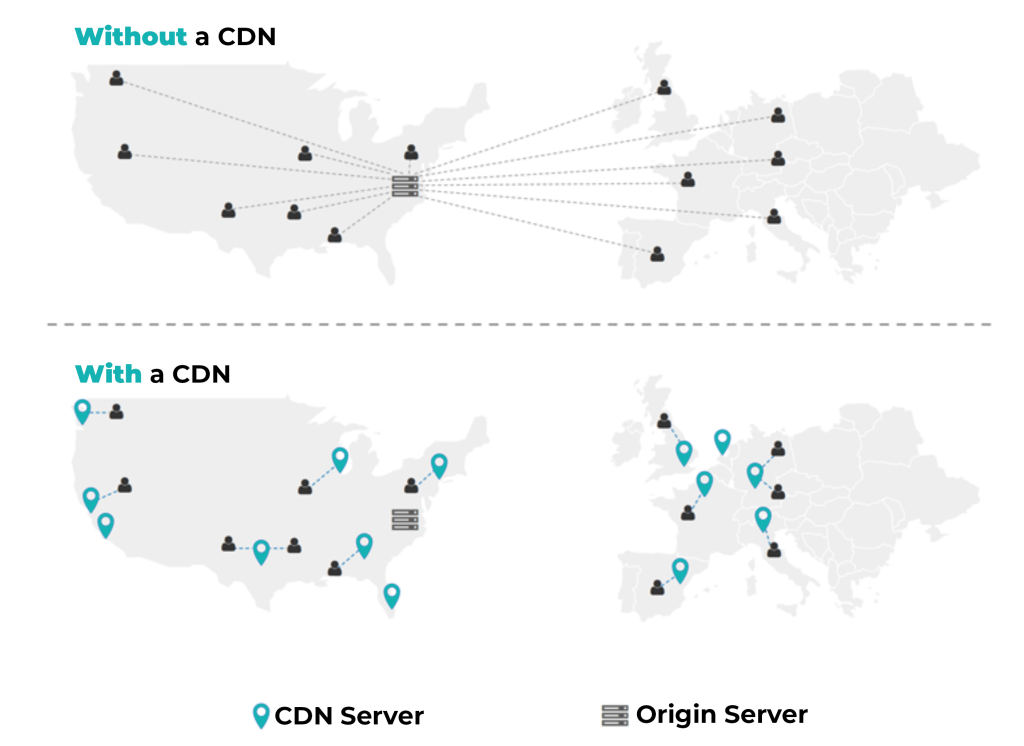
For our customers, integrating DataDome at the CDN/edge level is the best path for protection. That way, the scalability of the protection will be handled by the CDN platform as well, so when attacks occur, they will be distributed across ~100 points of presence (PoPs), with the CDN handling the traffic rather than the origin.
By comparison, using server side modules (for example, a web server like Nginx/HAProxy) or application modules (like ASP.NET/NodeJS) would mean that the attack would be received by the origin and the origin would not scale. So, a large attack would crash the website.
Our customers need to ensure…