Hidden Botnet C&C on Legitimate Infrastructure? The Case of 000webhostapp[.]com
Note: Thanks to Dancho Danchev, WhoisXML API’s DNS Threat Researcher, for the initial investigation available here, which led to the creation of this post.
Threats can come from anywhere, even from legitimate hosting infrastructure. In fact, many cybercriminals often host their command-and-control (C&C) servers in known hosting providers’ networks, sometimes those that offer bulletproof hosting services, to evade detection and consequent blocking.
We found that one service provider that has been recently abused by cyber attackers is Hostinger. Two WhoisXML API studies specified 93 IP addresses, 119 subdomains of the domain 000webhostapp[.]com, and four name servers, all part of Hostinger’s infrastructure, that have played a part in botnet operations.
We used a variety of domain and IP intelligence tools to obtain as much information as possible on these to help cybersecurity teams better protect their networks.
IP Address Resolutions
We subjected the 93 IP addresses to reverse IP/DNS lookups to determine how many and what domains they resolved to over time according to passive Domain Name System (DNS) data.
The 93 IP addresses resolved to at least 300 domains each, amounting to a total of at least 27,900 domains. Note that the results of the reverse IP/DNS lookups we did listed only up to 300 domains per IP address queried even if there could be more resolutions.
After removing duplicate domains, we ended up with a list of 8,416. Of these, 48% (totaling 4,015 domains) use the .com top-level domain. In second and third place are .xyz (6% or 520) and .online (5% or 393) domains, respectively. The top 20 TLDs are shown in Chart 1 below.
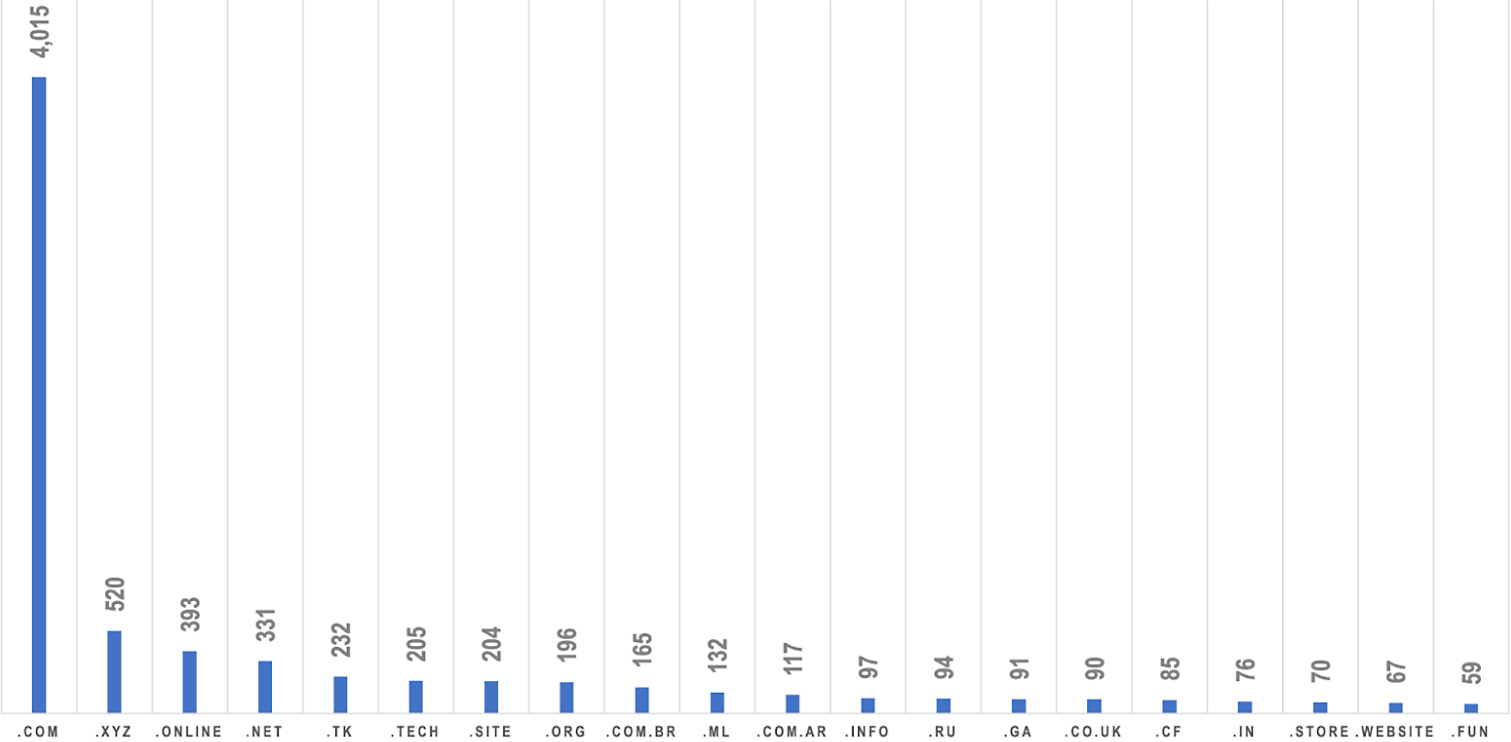
Based on the data shown in Chart 1, it may be best for organizations that don’t want to employ IP-level blocking of the Hostinger IP addresses related to the campaign, to instead be especially wary of connected domains sporting the top 20 TLDs mentioned above. Companies that use Hostinger or have partners and customers that do may be among those who wouldn’t want to block the IP addresses. Some of these could have been hijacked by the…