Authorities Claim LockBit Admin “LockBitSupp” Has Engaged with Law Enforcement
LockBitSupp, the individual(s) behind the persona representing the LockBit ransomware service on cybercrime forums such as Exploit and XSS, “has engaged with law enforcement,” authorities said.
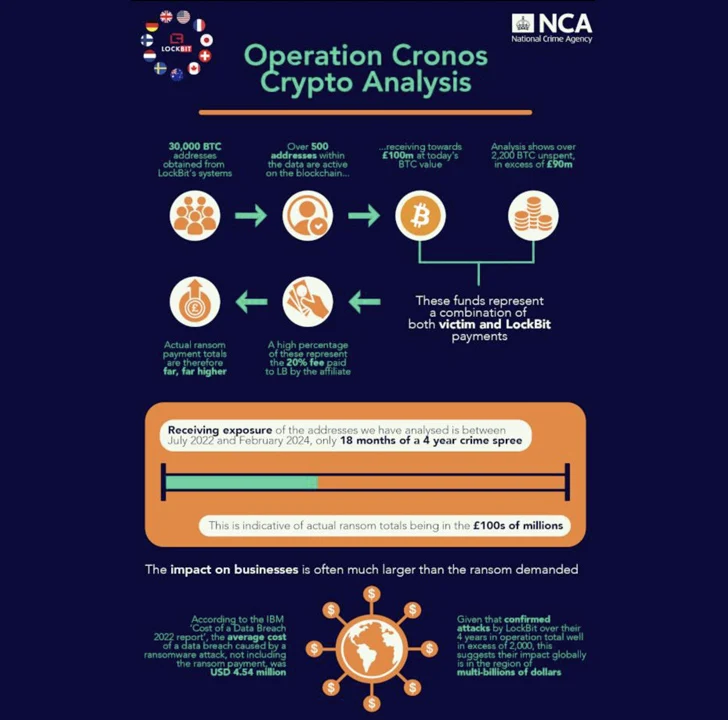
The development comes following the takedown of the prolific ransomware-as-a-service (RaaS) operation as part of a coordinated international operation codenamed Cronos. Over 14,000 rogue accounts on third-party services like Mega, Protonmail, and Tutanota used by the criminals have been shuttered.
“We know who he is. We know where he lives. We know how much he is worth. LockbitSupp has engaged with law enforcement,” according to a message posted on the now-seized (and offline) dark web data leak site.
The move has been interpreted by long-term watchers of LockBit as an attempt to create suspicion and sow the seeds of distrust among affiliates, ultimately undermining trust in the group within the cybercrime ecosystem.
According to research published by Analyst1 in August 2023, there is evidence to suggest that at least three different people have operated the “LockBit” and “LockBitSupp” accounts, one of them being the gang’s leader itself.
However, speaking to malware research group VX-Underground, LockBit stated “they did not believe law enforcement know his/her/their identities.” They also raised the bounty it offered to anyone who could message them their real names to $20 million. It’s worth noting that the reward was increased from $1 million USD to $10 million late last month.
LockBit – also called Gold Mystic and Water Selkie – has had several iterations since its inception in September 2019, namely LockBit Red, LockBit Black, and LockBit Green, with the cybercrime syndicate also secretly developing a new version called LockBit-NG-Dev prior to its infrastructure being dismantled.
“LockBit-NG-Dev is now written in .NET and compiled using CoreRT,” Trend Micro said. “When deployed alongside the .NET environment, this allows the code to be more platform-agnostic. It removed the self-propagating capabilities and the ability to print ransom notes via the user’s printers.”
One of the notable additions is the inclusion of a validity period, which continues its operation only if the…