Agenda ransomware threatens to resurface

Stephen Osler, co-founder and business development director, Nclose.
The Agenda ransomware, which quickly gained notoriety for being able to trigger customised ransomware attacks at intended targets, is on the radar again. Cyber security experts warn of the threat to South African sectors, particularly healthcare and education.
Agenda was created in the Go open source programming language (Golang) developed by Google. It was first detected in late 2022 in Indonesia, Thailand, Saudi Arabia, and South Africa, but seemed to have become dormant – until now.
According to market research by Trend Micro there have been a few incidents at the beginning of 2023, serious enough for cyber security experts to issue another warning that organisations cannot afford to let their guard down.
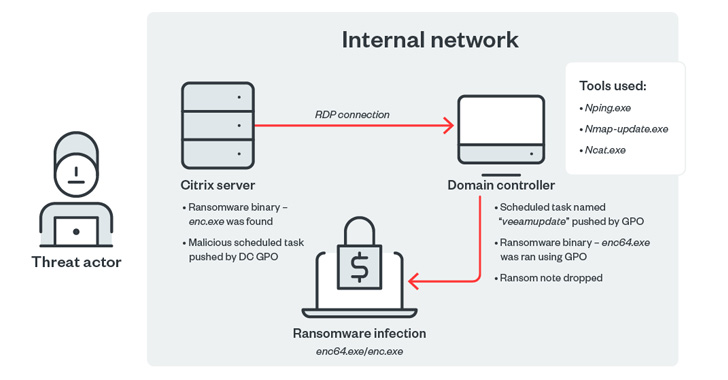
This is mainly because of the ransomware’s sophisticated capabilities. They enable Agenda to bypass antivirus processes, change passwords, encrypt data, and gain unauthorised access to systems using new credentials. If undetected and not contained, it has the potential to bring down networks, says Trend Micro.
Stephen Osler, co-founder and business development director at cyber security specialist Nclose, says as is the case with most ransomware tools, Agenda takes advantage of poor security practices, weak passwords, and inadequate system patching.
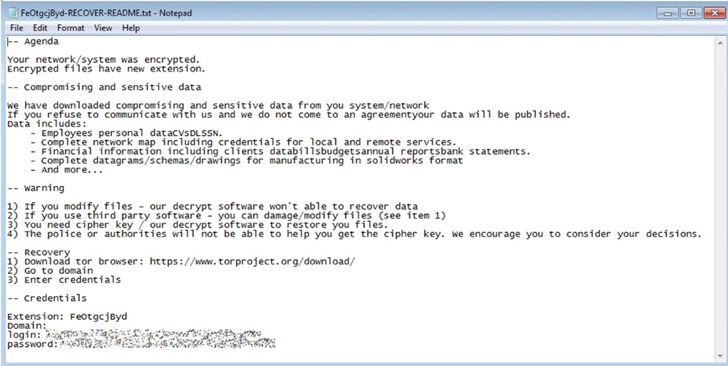
It also has built-in tools and algorithms that enable it to encrypt files using a string of random characters as a file extension. This file contains a ransom note detailing threats or leaks of sensitive information if the ransom isn’t paid. It also includes warnings of additional consequences if attempts are made to decrypt the files.
“So, the severity is high, and threat is high from the start,” says Osler.
South Africa a prime target
South Africa has consistently been the primary target for ransomware and business e-mail compromise among African countries, Nclose notes.
The company refers to the latest State of Ransomware report by Sophos, which states that 78% of the South African companies surveyed reported being subjected to a ransomware attack in the past year. This represents a notable increase from the 51% reported in the…