US prison allegedly hit by ransomware attack
In what might be considered the first ransomware attack of its kind, the Play ransom gang claims to have successfully hit a maximum-security detention center in the Northeast state of Rhode Island.
The Donald W. Wyatt Detention Facility, located in the City of Central Falls, Rhode Island was listed on the threat actors dark leak site Tuesday evening.
The maximum-security facility at capacity houses over 700 adult males and 40 adult female detainees, according to Central Falls.
Detainees include those in custody by the US Marshals Service, the Federal Bureau of Prisons, the United States Navy, as well as those from the nearby Native American Mashantucket Pequot Reservation.
The threat group claims to have exfiltrated “Private and personal confidential data, clients documents, agreements, budget, HR, IDs, tax, finance information and etc.”
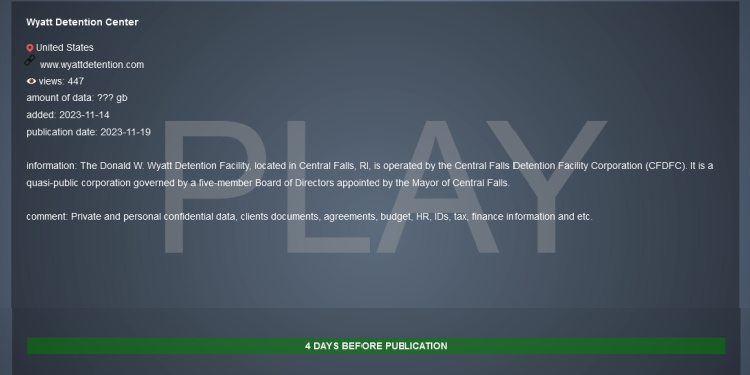
Play did not reveal the amount of stolen data it may have acquired from the Facility, instead cryptically posting three question marks “???” followed by a gigabyte symbol in the listing.
The gang also claims it will publish whatever data it has by a November 19th deadline.
Unlike a federal prison, the state detention center holds prisoners who have not yet been arraigned, have been denied bail, or are awaiting trial.
The private Facility is also governed by a board of directors appointed by the Central Falls Mayor, making it a quasi-public corporation.
Besides security systems and operations at the detention facility, files on inmates, especially those that may be found innocent, could supply the hackers with a treasure trove of information that could potentially be used to blackmail detainees in the future.
Additionally, for those inmates awaiting trial, sensitive documents could be used to sway legal proceedings and spur dozens of lawsuits against the Facility for failing to keep personal data secured.
Deemed part of the American Correctional Association (ACA), the Facility takes in prisoners from various jurisdictions, including the surrounding states of Connecticut, Massachusetts, New Hampshire, Maine, and Vermont.
Cybernews has reached out to the The Donald W. Wyatt Detention Facility, as well as…