Microsoft Disabled App Installer Abused by Hackers
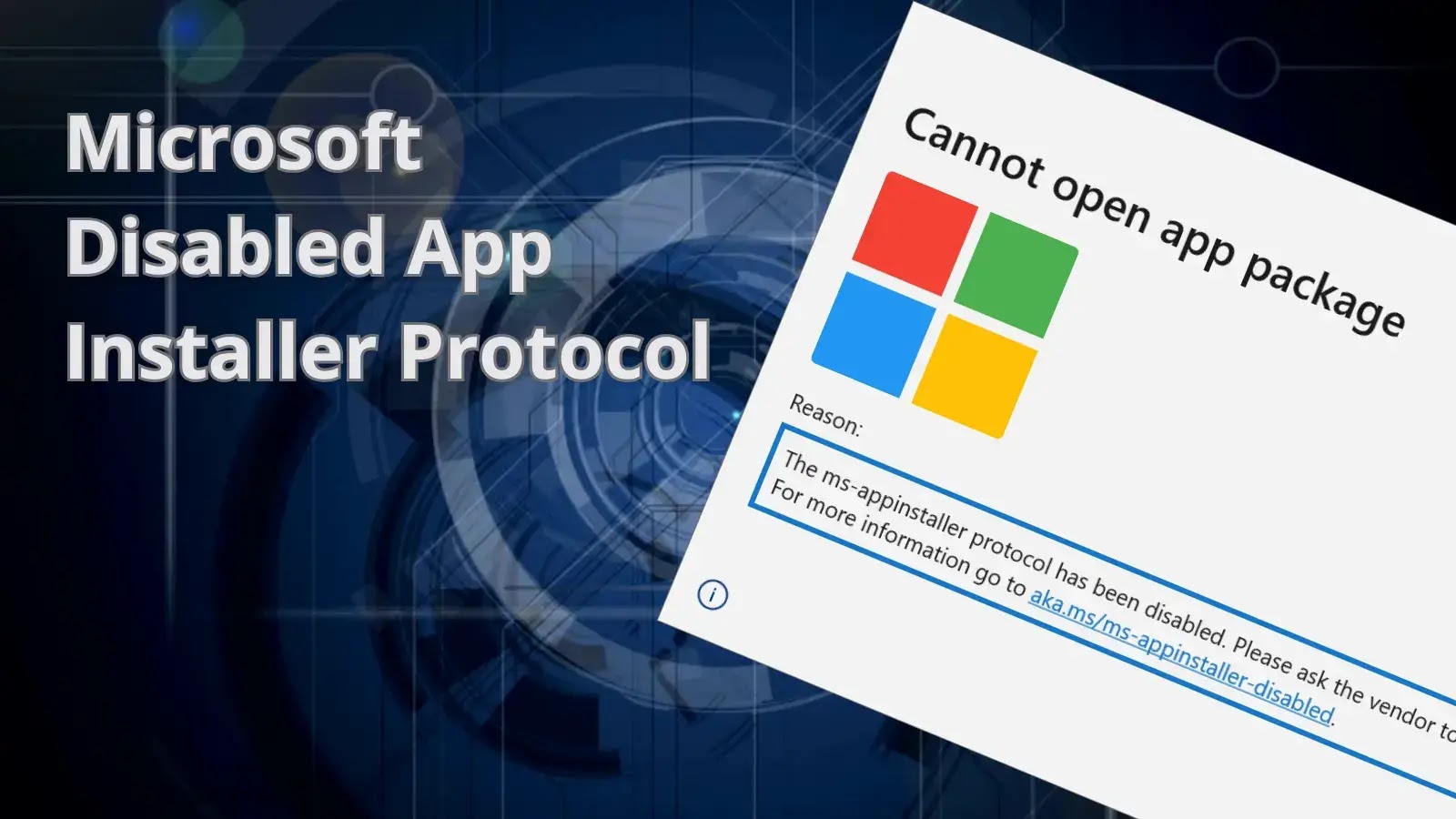
Threat actors, particularly those with financial motivations, have been observed spreading malware via the ms-appinstaller URI scheme (App Installer). As a result of this activity, Microsoft has disabled the ms-appinstaller protocol handler by default.
“The observed threat actor activity abuses the current implementation of the ms-appinstaller protocol handler as an access vector for malware that may lead to ransomware distribution,” the Microsoft Threat Intelligence team said.
The ms-appinstaller protocol handler vector is probably the one that threat actors have selected since it can bypass security measures like Microsoft Defender SmartScreen and built-in browser alerts for downloading executable file types, which are intended to protect users from malware.
Microsoft Threat Intelligence has identified App Installer as a point of entry for human-operated ransomware activities by several actors, including Storm-0569, Storm-1113, Sangria Tempest, and Storm-1674.
Compounding the problem are zero-day vulnerabilities like the MOVEit SQLi, Zimbra XSS, and 300+ such vulnerabilities that get discovered each month. Delays in fixing these vulnerabilities lead to compliance issues, these delay can be minimized with a unique feature on AppTrana that helps you to get “Zero vulnerability report” within 72 hours.
Spoofing legitimate applications, tricking users into installing malicious MSIX packages that look like legitimate applications, and avoiding detections on the initial installation files are some of the activities that have been noticed.
Financially Motivated Threat Actors Abusing App Installer
Microsoft discovered that Storm-0569 was using search engine optimization (SEO) poisoning to spread BATLOADER by impersonating websites that offered legitimate downloads, including AnyDesk, Zoom, Tableau, and TeamViewer.
When a user searches on Bing or Google for a legitimate software application, they could see links to malicious installers using the ms-app installer protocol on a landing page that mimics the landing pages of the actual software provider. A prominent social engineering technique involves spoofing and imitating…