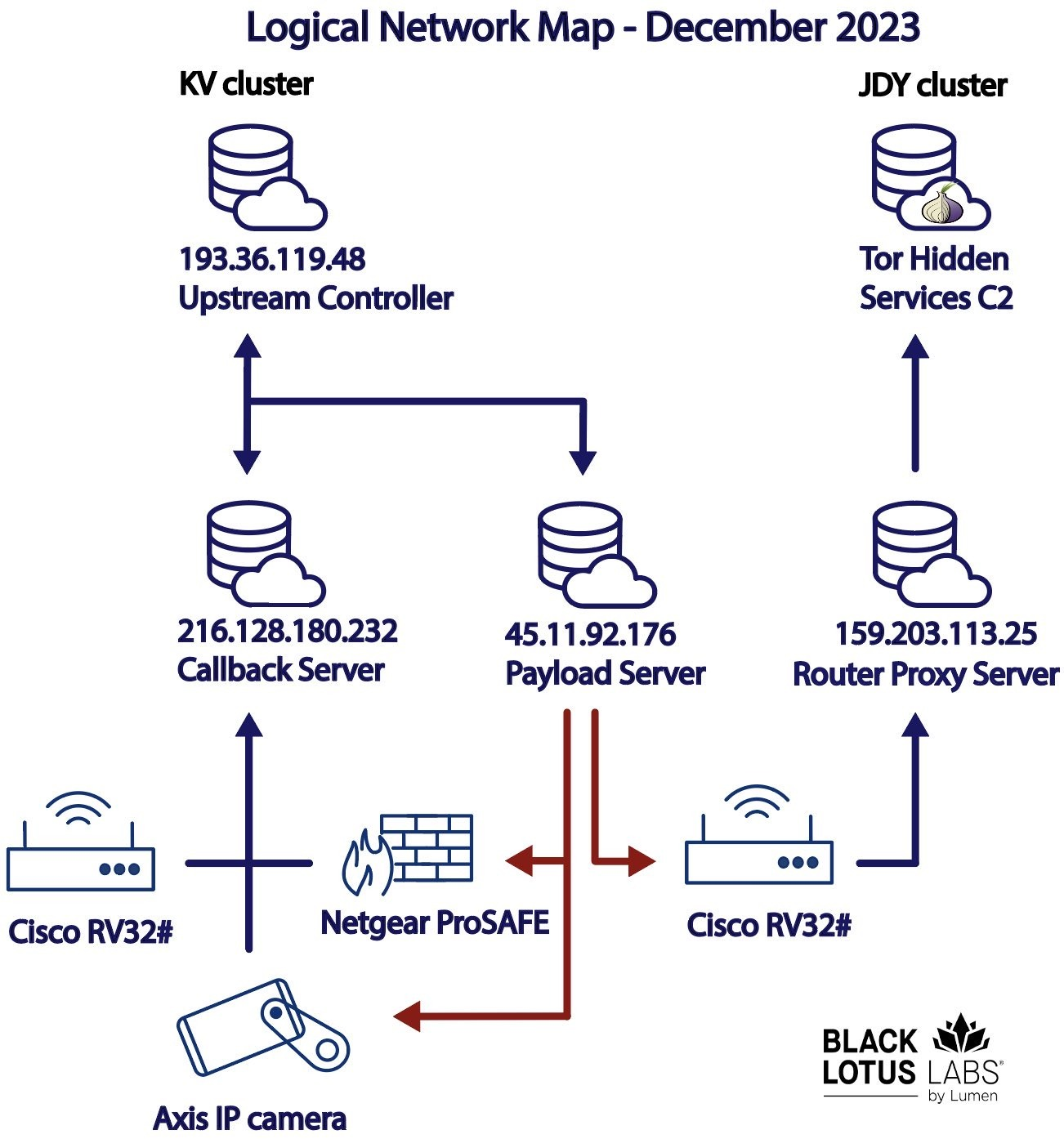
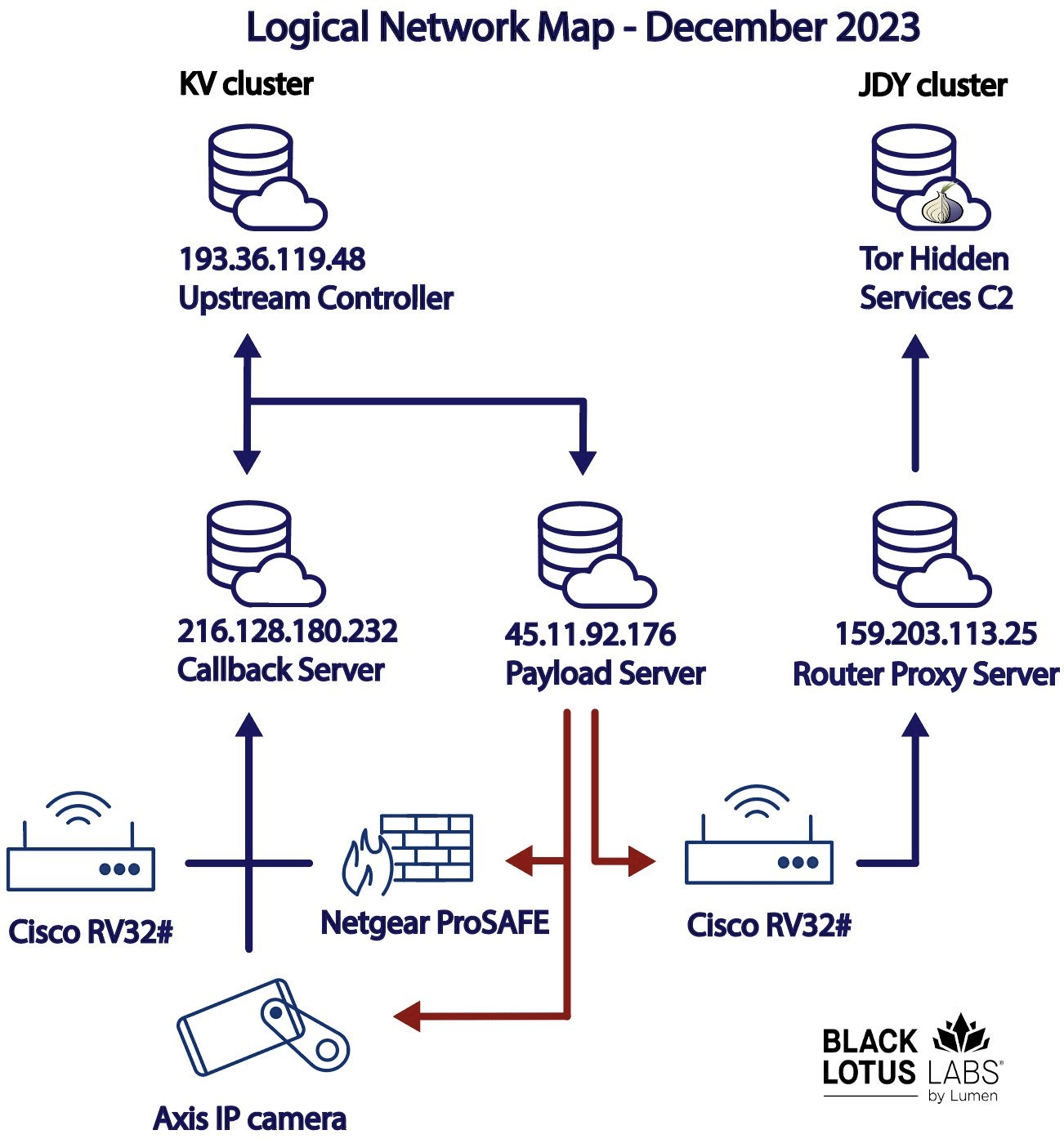
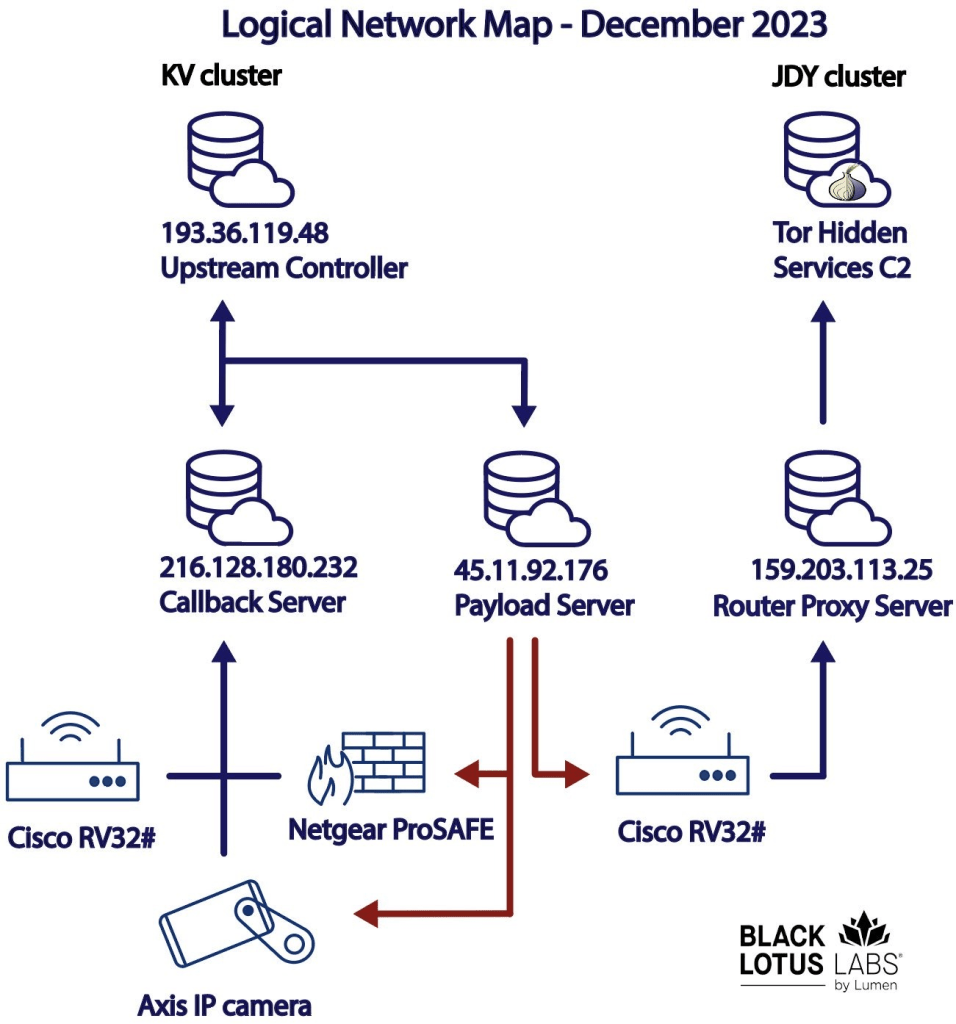
Vedalia APT Group Exploits Oversized LNK Files to Malware
The Vedalia Advanced Persistent Threat (APT) group, also known by its alias Konni, has been distributing malware using an innovative technique involving oversized LNK files.
This method marks an evolution in the group’s operational tactics, aiming to bypass conventional security measures and compromise targeted systems.
Broadcom recently published a blog post stating that the Vedalia APT group has utilized huge LNK files in their latest malware campaign.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Try Trustifi Free Threat Scan with Sophisticated AI-Powered Email Protection .
Key Highlights of the Campaign
- Innovative Delivery Mechanism: The Vedalia APT group has ingeniously utilized LNK files with double extensions, effectively masking the malicious .lnk extension.
- This tactic deceives users into believing the files are harmless, increasing the likelihood of execution.
- Obscuration through Whitespace: A notable characteristic of these LNK files is the excessive use of whitespace.
- This technique is designed to hide the malicious command lines embedded within, making detection by security software and analysts more challenging.
- Bypassing Security Defenses: The embedded command line script within the LNK files is crafted to search for and execute PowerShell commands.
- This approach is specifically chosen to evade detection mechanisms. It leverages PowerShell’s legitimate system functions to locate and deploy the embedded malicious files and payload.
File-based
- CL.Downloader!gen20
- Scr.Mallnk!gen13
- Trojan.Gen.NPE
- WS.Malware.1
Implications and Recommendations
The Vedalia APT group’s adoption of oversized LNK files for malware delivery underscores the evolving landscape of cyber threats.
Organizations and individuals are advised to remain vigilant, update their security solutions, and educate users about the risks of opening files from unknown sources.
This campaign by the Vedalia APT group serves as a reminder of the continuous innovation among cyber adversaries.
By staying informed and proactive, organizations…