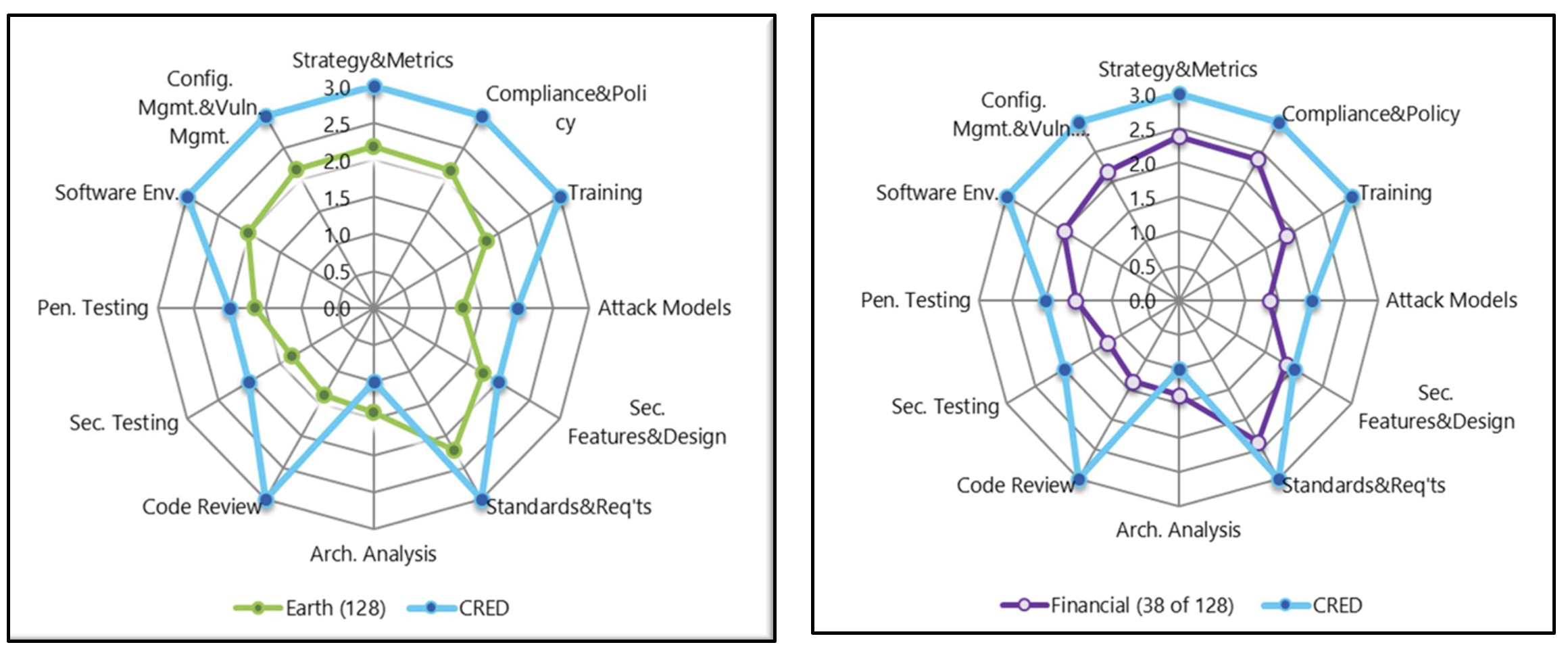
Spotlight on CRED: Benchmarking security with a BSIMM assessment
CRED, a fintech company and BSIMM member since early 2022, underwent a BSIMM assessment to benchmark their security processes.
CRED, launched in 2018, provides financial services and lifestyle features, and has been a member of the BSIMM community since early 2022. CRED provides a wide variety of product offerings from lifestyle to personal finance. It has a strong ethos of upholding and meeting client’s demands, and the #SecurityFirst culture at CRED has been ingrained into its culture from its start.
The challenge
The security team at CRED strongly believes in building a great team of engineers and in the importance of establishing a strong information security presence. The team is involved in research and development of CRED’s ever-growing security ecosystem. CRED’s security culture includes:
Advanced learning sessions: Each week, team members conduct research into emerging security flaws and lead educational sessions for the security team. These sessions include a deep dive into new security vulnerabilities, how they can be exploited, their mitigations, and a capture-the-flag challenge for team members to fully understand the vulnerability.
- Threat modeling: For each new feature or product release, CRED’s security team conducts a security threat modeling exercise to identify potential design flaws, edge cases, data flows, and architecture choices, all of which could result in certain risks to the company.
- Security Bugbash: This gamified exercise is performed once a quarter to look for new vulnerabilities or threats in the CRED application. This introduces fresh perspectives, inventive exploitation scenarios, and approaches that aid in the team’s search for bugs and security flaws.
- Capture-the-flag competition: Hackception is a company-wide information security competition hosted by the security team. Participating in Hackception helps developers think creatively about how to exploit software, and how to code securely.
- Security hackathon: During this event, the team brainstorms new automation that can reduce recurring manual efforts and identifies projects that could improve the team’s security maturity. This practice drastically reduces manual effort in security…