Data protection in 2023 was all about resilience – Blocks and Files
Recovering from data loss and ransomware are the gifts that keep on giving … for data protection suppliers, that is.
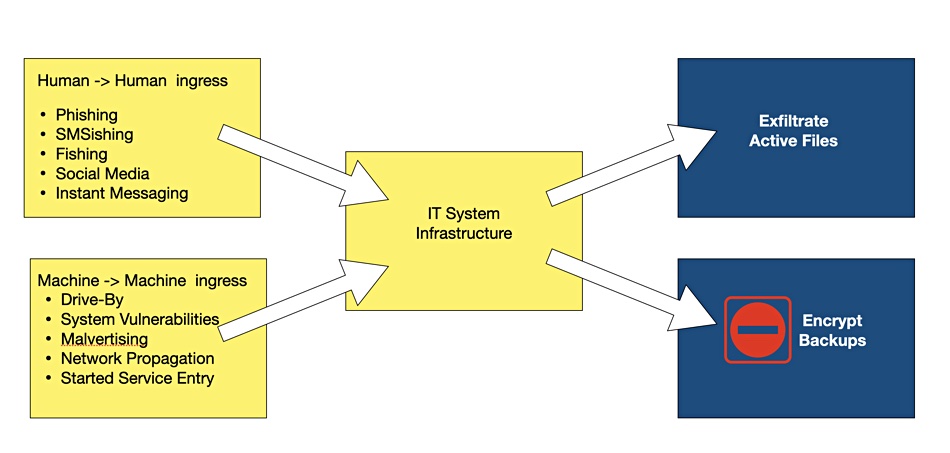
Compared to a year ago, there is now more data to protect and more threats against it, making favorable market conditions for the suppliers. The data protection world in 2023 was dominated by dealing with cyber resilience, extending backup’s remit to cover SaaS applications, and seeking new archive technologies to fix tape’s flaws.
Virtually every backup supplier has now added security features to protect against ransomware and other malware attacks on data. Cyber resilience is the name of the backup game, and resilience is starting to look like an over-used word. For example:
- Veeam describes itself as the home of radical resilience.
- Cohesity says: “Protection is one thing. Resilience is everything.”
- Commvault claims it “gives you an unfair advantage to ensure resilience in the face of ransomware and other advanced threats in today’s hybrid world – and tomorrow’s.”
- Druva says it is “the industry’s leading SaaS platform for data resiliency, and the only vendor to ensure data protection across the most common data risks backed by a $10 million guarantee.”
- Rubrik greets its website visitors with this message: “Rubrik Security Cloud delivers complete cyber resilience.”
- Veritas tells its site visitors: “We have a reputation for reliability at scale, which delivers the resilience our customers need against the disruptions threatened by cyberattacks, like ransomware.”
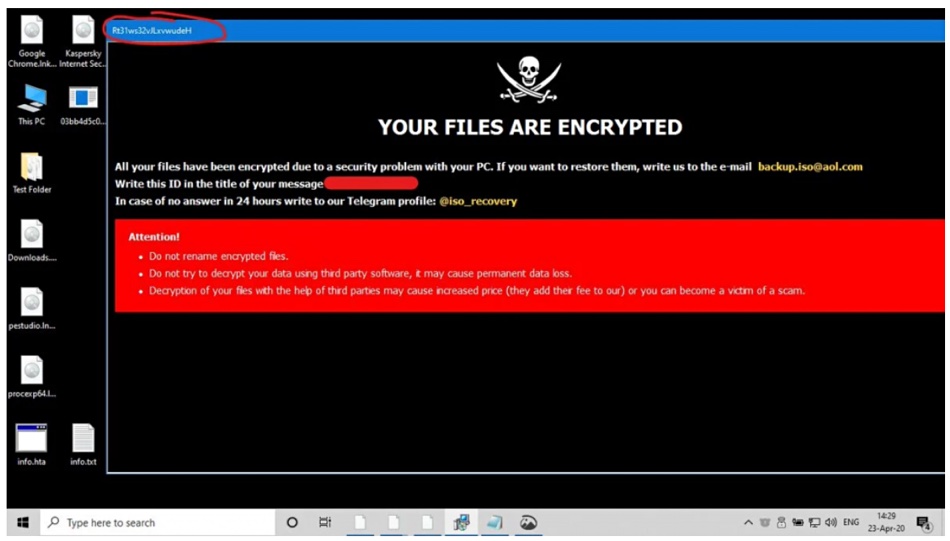
To keep protected data resilient, suppliers typically offer immutable backups and backup health checks, providing known good files, for example. Focus has extended from ransomware attack prevention to ransomware attack recovery, with some guarantees that such recovery is dependable.
No magic anti-malware silver technology bullet was announced in 2023 by any supplier – because there isn’t one.
SaaS app protection
Technology additions were sought by SaaS app protectors, spearheaded by HYCU. It realized that many SaaS applications stored customer data that was not protected by the provider or by data…