Exploited TP-Link Vulnerability Spawns Botnet Threats
Endpoint Security
,
Governance & Risk Management
,
Internet of Things Security
Attackers Exploit Old Flaw, Hijack TP-Link Archer Routers

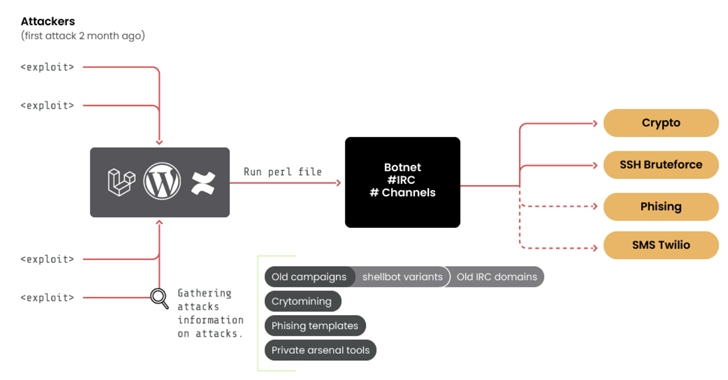
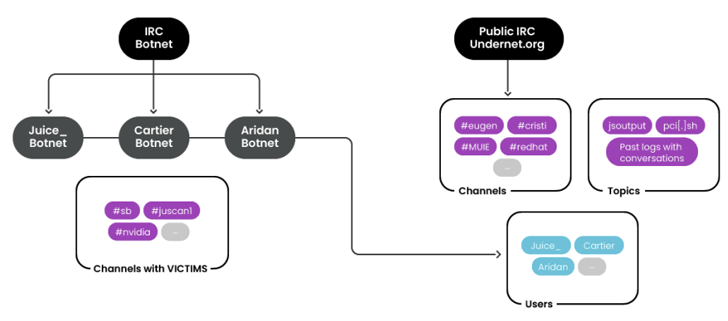
Half a dozen different botnets are prowling the internet for TP-Link-brand Wi-Fi routers unpatched since last summer with the goal of commandeering them into joining distributed denial-of-service attacks.
See Also: Cyber Hygiene and Asset Management Perception vs. Reality
Chinese router manufacture TP-Link in June patched a command injection vulnerability in its Archer AX21 router, a residential model that retails for less than $100. Consumer-grade routers are notorious for uneven patching, either because manufacturers are slow to develop patches or consumers don’t apply them. “Once they’re connected to the internet, they don’t care anymore about the router,” one industry CISO told Oxford University academics researching a 2023 paper.
The vulnerability, tracked as CVE-2023-1389, allows attackers to insert malicious commands by calling the “locale” API on the web management interface. Attackers use set_country to insert remote code since the unpatched routers don’t sanitize that input.
Researchers at Fortinet said Tuesday they’ve observed multiple attacks over the past month focused on exploiting the vulnerability – including botnets Moobot, Miori, the Golang-based agent “AGoent,” a Gafgyt variant and an unnamed variant of the infamous Mirai…