LockBit, Cl0P expand ransomware efforts
LockBit in the lead, CL0P in 2nd
The report, Ransomware on the Move, looked at how exploitation techniques are evolving — including attackers’ sharpened focus on zero-day vulnerabilities. It showed how victims of multiple ransomware attacks were more than six times more likely to experience the second attack within three months of the first attack.
The authors from Akamai’s Security Intelligence Group reviewed data from the fourth quarter of 2021 to the second quarter of 2023. The authors reported that LockBit ensnared around 39% of all victim organizations tracked by Akamai, which said LockBit’s victim count is three times that of its nearest competitor, the CL0P group. Number three in volume of victims, ALPHV, aka Black Cat, focused its efforts on developing and exploiting zero-day points of entry (Figure A).
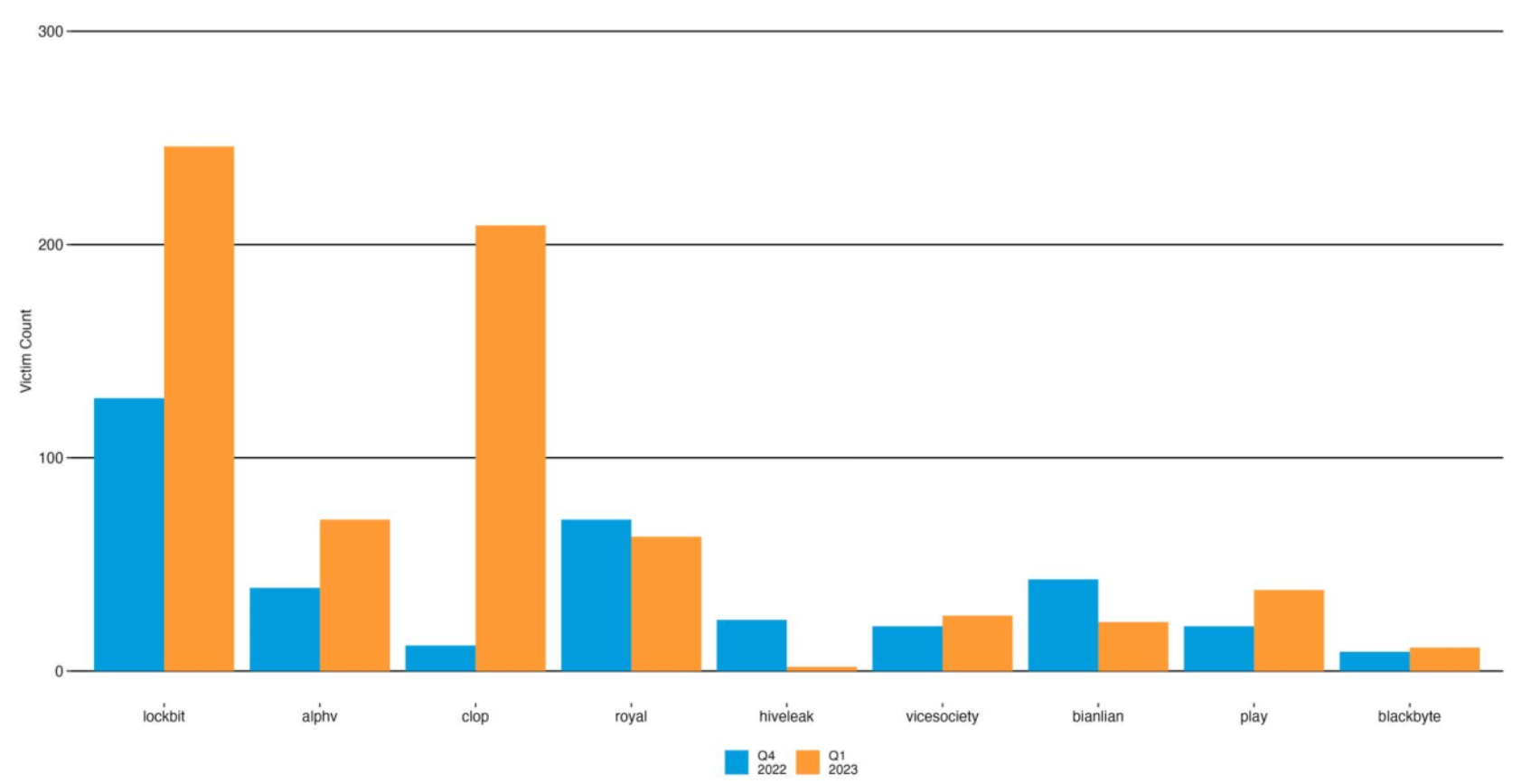
- Top ransomware groups by victim count. Source: Akamai.
Anthony Lauro, director of security technology and strategy at Akamai, explained that LockBit looks for high value targets with zero day vulnerabilities that companies can’t fix quickly. They tend to target and retarget these organizations and the sectors — like manufacturing and technology for example — where security operations are lagging, generally. Also, he explained, malware writers can choose tools and services from a growing dark ecosystem.
2 clear trends show how threats are evolving
The report spotlighted two trends that speak to how large groups — with reach and breadth of products including RaaS — have a stable growth and smaller groups focus on opportunities as they arise:
- The first is exemplified by LockBit, characterized by a steady count of 50 victims per month, and activity seems tied to its number of affiliates and its resources.
- The second, typified by groups like CL0P, feature spikes in activity from abusing critical zero-day vulnerabilities as they appear, and highly targeted security flaws.
“Malware writers can now split off operations, which is a change,” said Lauro. “It used to be that the attackers were a single entity or group that would be responsible for malware payload delivery, exploitation and follow up.” He added that, because of the open nature of the…