Tag Archive for: code
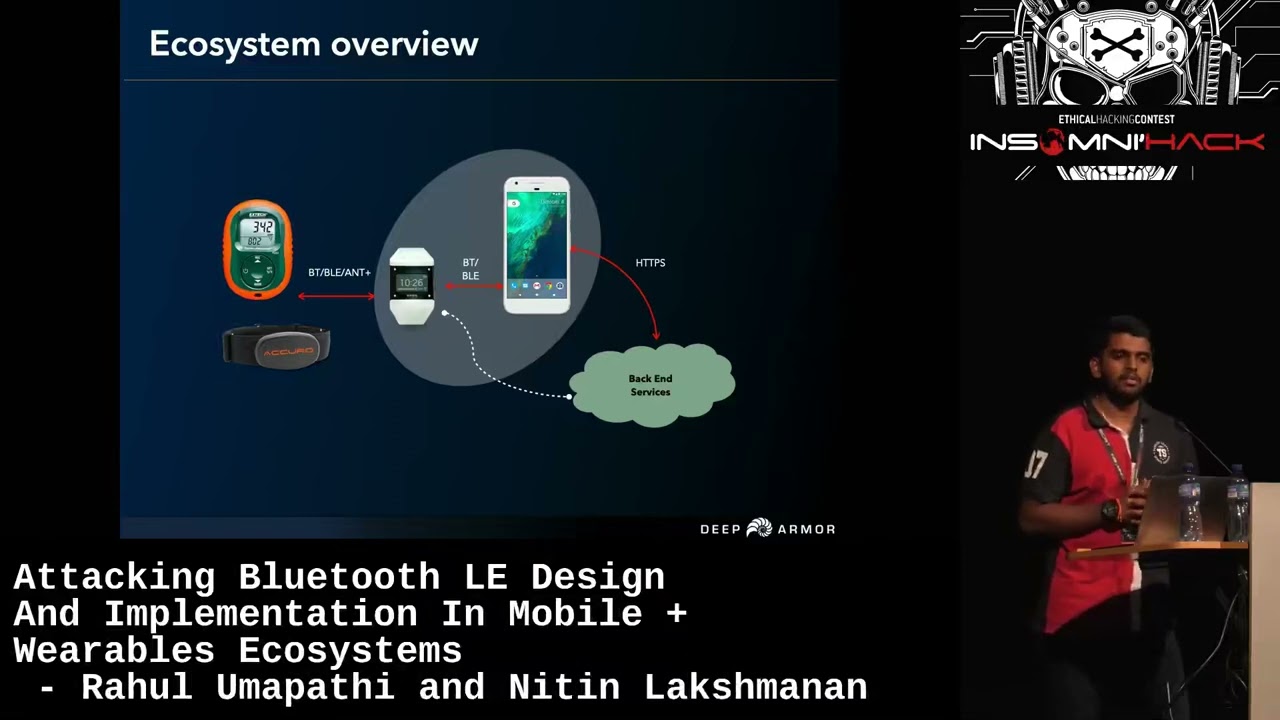
Attacking Bluetooth LE Design And Impl In Mobile Wearables by Rahul Umapathi and Nitin Lakshmanan
/in Video
Breaking Down the Code: Computer Scientists Untangle Internet’s Complex Protocols to Unveil Underlying Simplicity
/in Internet Security
Undergraduate students taking computer-networking courses often find themselves confronted with an avalanche of acronymic protocols that dictate how the internet works. But underlying the layers of complexity, there exists surprising simplicity in the design of the internet, as illustrated in the February cover feature for Communications of the ACM (Association for Computing Machinery) — a monthly magazine published by the world’s largest educational and scientific computing society.
Looking to cut through that seemingly tangled mess, UCLA computer science professor George Varghese, joined by his colleagues James McCauley of Mount Holyoke College in Massachusetts and Scott Shenker of UC Berkeley, set out to explain in this article that the internet’s fundamental design has remained unchanged since its adoption in 1983.
Titled “Extracting the Essential Simplicity of the Internet,” the predominantly non-technical article boils down the internet’s architecture to three key mechanisms: routing, reliability and resolution. They formed the foundation of the ubiquitous global system of interconnected computer networks despite evolving technologies built around the internet.
“Most people understand the power of the internet but few appreciate the brilliance of its design that has allowed the system to accommodate decades of growth, with billions of users and connected devices that process mountains of data in a blink of an eye,” said Varghese, who holds UCLA’s Jonathan B. Postel Endowed Chair in Networking. He has made landmark contributions to network algorithmics, which helped make the internet run faster. His current research emphasis is on network design automation, to help manage and debug computer networks.
The article originated from a guest lecture by Shenker on the internet’s basic routing simplicity in a UCLA undergraduate networking class taught by Varghese. The internet’s long-lasting success, the authors noted, can be attributed to its modest all-purpose design; its modularity that allows it to incorporate innovations at the applications end that are completely distinct from the connecting network layers; and its built-in layers of fail-safe…
Leaked LockBit, Babuk code leveraged by Buhti ransomware operation
/in Internet Security
Attacks by Blacktail on Windows systems involve the use of the Windows LockBit 3.0 builder that would prompt file encryption with the “.buthi” extension, while a Babuk source code-based payload has been leveraged in intrusions against Linux systems, according to a report from Symantec’s Threat Hunter team.
Despite reusing leaked ransomware source code, Blacktail’s Buhti operation has been leveraging its own Go-based exfiltration tool and network infiltration technique on top of exploiting the PaperCut NG and MF remote code execution vulnerability, tracked as CVE-2023-27350, and the IBM Aspera Faspex flaw, tracked as CVE-2022-47986, said researchers.
Organizations in the U.S., China, Belgium, India, Estonia, Switzerland, Spain, Germany, Ethiopia, and the U.K. have already been impacted by Buhti ransomware attacks, indicating the significant threat of the Blacktail operation, noted Kaspersky researcher Marc Rivero.