A Look into Top Couriers’ Digital Footprint
Just as no man is an island, no company can perform core functions without other organizations’ help. This fact is highlighted in today’s age of outsourcing, partnership, and third-party connections. Unfortunately, threat actors have also found a massive opportunity in these relationships. Targeting a third-party vendor often allows them to target the vendor’s clientele.
In this post, we used our Third-Party Risk Management (TPRM) solutions to look at some of the popularly used express mail courier services that several companies worldwide partner with — FedEx, DHL, China Post, and UPS. These companies are often targeted since they have thousands, if not millions, of personally identifiable information (PII) in their records. In August 2020, for example, a Canadian courier became a victim of a ransomware attack, giving threat actors access to its customers’ personal details.
Potential “Unknowns” in the Digital Footprint of FedEx, DHL, China Post, and UPS
We gathered a total of 24,601 domains and subdomains containing the words “fedex,” “dhl,” “chinapost,” and “ups.” A vast majority of the subdomains were not owned by any of the courier companies, as confirmed by a bulk WHOIS lookup.
Indeed, only 40 domains appeared to be managed by the legitimate companies, as they matched WHOIS record details with the official couriers’ domain names. This number represents less than 1% of the total number of subdomains in our dataset. The table below shows the breakdown.
| Company | # of domains with matching WHOIS record details | Percentage match |
|---|---|---|
| UPS | 38 | 0.15% |
| DHL | 1 | 0.00% |
| FedEx | 1 | 0.00% |
| China Post | 0 | 0.00% |
TLD
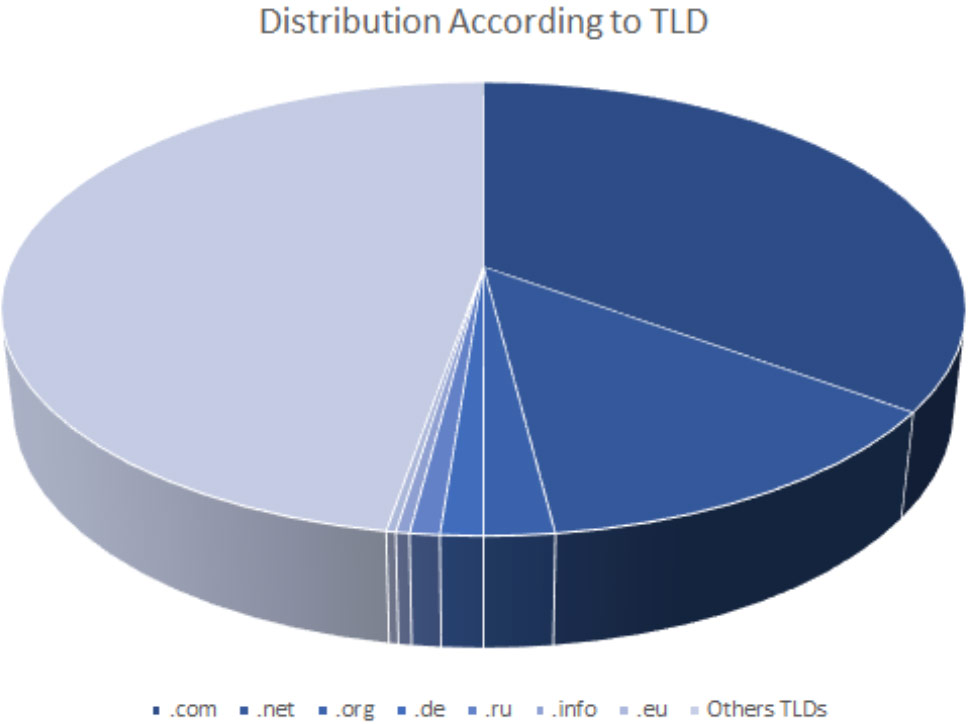
We studied the top-level domain (TLD) distribution of the domains and subdomains obtained and ran them against the most abused TLDs known to direct visitors to phishing and botnet command-and-control (C&C) servers. Seven of the most abused TLDs made up more than half (53%) of the total number of subdomains.
The pie chart shows the TLD distribution of the subdomains under the .com, .net, .org, .de, .ru, .info, and .eu TLDs against all other TLDs not included in the list of most abused.
All seven TLDs were among the most abused by botnet operators. The .com TLD was also most favored by…