Critical Flaws Leave 92,000 D-Link NAS Devices Vulnerable to Malware Attacks
Threat actors are actively scanning and exploiting a pair of security flaws that are said to affect as many as 92,000 internet-exposed D-Link network-attached storage (NAS) devices.
Tracked as CVE-2024-3272 (CVSS score: 9.8) and CVE-2024-3273 (CVSS score: 7.3), the vulnerabilities impact legacy D-Link products that have reached end-of-life (EoL) status. D-Link, in an advisory, said it does not plan to ship a patch and instead urges customers to replace them.
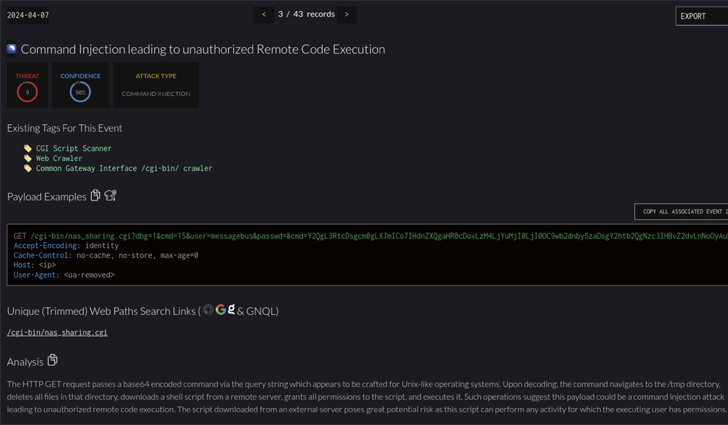
“The vulnerability lies within the nas_sharing.cgi uri, which is vulnerable due to two main issues: a backdoor facilitated by hard-coded credentials, and a command injection vulnerability via the system parameter,” security researcher who goes by the name netsecfish said in late March 2024.
Successful exploitation of the flaws could lead to arbitrary command execution on the affected D-Link NAS devices, granting threat actors the ability to access sensitive information, alter system configurations, or even trigger a denial-of-service (DoS) condition.
The issues affect the following models –
- DNS-320L
- DNS-325
- DNS-327L, and
- DNS-340L
Threat intelligence firm GreyNoise said it observed attackers attempting to weaponize the flaws to deliver the Mirai botnet malware, thus making it possible to remotely commandeer the D-Link devices.
In the absence of a fix, the Shadowserver Foundation is recommending that users either take these devices offline or have remote access to the appliance firewalled to mitigate potential threats.
The findings once again illustrate that Mirai botnets are continuously adapting and incorporating new vulnerabilities into their repertoire, with threat actors swiftly developing new variants that are designed to abuse these issues to breach as many devices as possible.
With network devices becoming common targets for financially motivated and nation-state-linked attackers, the development comes as Palo Alto Networks Unit 42 revealed that threat actors are increasingly switching to malware-initiated scanning attacks to flag vulnerabilities in target networks.
“Some scanning attacks originate from benign networks likely driven by malware on infected machines,”…