Florida Memorial University reportedly targeted in ransomware cyberattack | South Florida News
Florida Memorial University (FMU), South Florida’s only historically Black college or university has reportedly fallen victim to a cybersecurity breach by the ransomware group known as INC Ransom. The specifics of the data compromised during this incident remain uncertain, and the university has yet to issue a formal statement regarding the breach.
INC Ransom posts on their blog confirming their recent attack on Florida Memorial University.
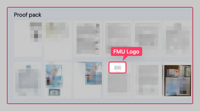
In a disturbing display of their malicious capabilities, INC Ransom has uploaded a ‘proof pack’ on its website, showcasing scans of passports, Social Security numbers, and contractual documents, ostensibly sourced from FMU’s databases.
INC Ransom has uploaded a so-called “proof pack” on its website, showcasing scans of passports, Social Security numbers, and contractual documents, ostensibly sourced from FMU’s databases.
…