Hunt Ransomware ([email protected]) – Decrypt Guide & Removal– Gridinsoft Blog
Hunt ransomware is a new sample of the Dharma/CrySis ransomware family that appeared on April 5, 2024. This malware aims at encrypting the files and asking a ransom payment for their decryption. It unselectively targets both home users and corporations, correcting the ransom depending on the target. Jakub Kroustek was the first to discover this malware.
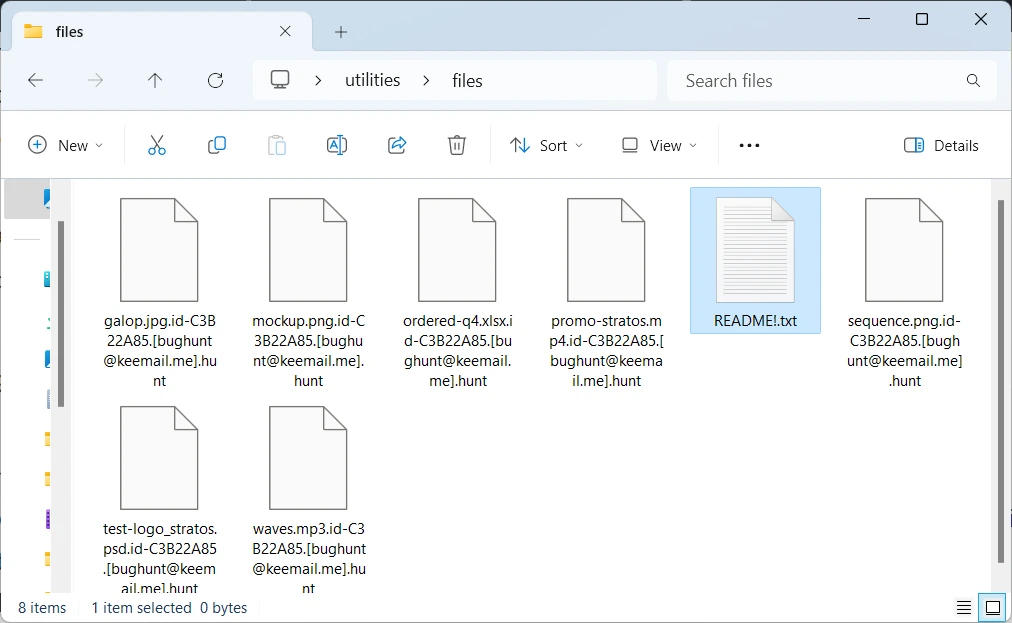
As I’ve said in the introduction, Hunt is a novice sample of the Dharma ransomware family. Being its part, Hunt ransomware follows its behavior patterns. The most noticeable one for the victim is the application of a complex extension, that contains the victim’s ID, the contact email (bughunt@keemail[.]me) and its .hunt extension. The files start looking as below after the encryption:
image.png → image.png.id-C3B22A85.[[email protected]].hunt
document.docx → document.docx.id-C3B22A85.[[email protected]].hunt
Hunt ransomware goes through the entirety of user disks, searching for the files it can encrypt. It is capable of ciphering the vast majority of ones, from images and videos to project files of specific software suites. However, this malware carefully avoids any system files – probably, to prevent system malfunctions that can potentially force the user into reinstalling the system.
Before applying the encryption, this malware disables built-in Windows backup options, such as Restore Points and Shadow Copies. They are rather useful for reverting the system state to pre-encryption, so such action is rather expected. Hunt ransomware uses the command you can see below to accomplish this.
vssadmin delete shadows /all /quiet
After finishing the encryption (i.e. it can’t find more unencrypted files), Hunt ransomware spawns a text file with a ransom note. It also opens an HTA file with the information about with more detailed information about what’s happened and instructions for the ransom payment. You can see the example of this pop-up…