TA866 Deploys WasabiSeed & Screenshotter Malware
The threat actor tracked as TA866 has resurfaced after a nine-month hiatus with a new large-volume phishing campaign to deliver known malware families such as WasabiSeed and Screenshotter.
The campaign, observed earlier this month and blocked by Proofpoint on January 11, 2024, involved sending thousands of invoice-themed emails targeting North America bearing decoy PDF files.
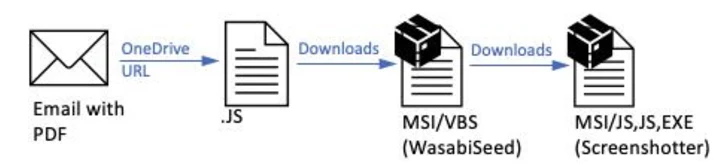
“The PDFs contained OneDrive URLs that, if clicked, initiated a multi-step infection chain eventually leading to the malware payload, a variant of the WasabiSeed and Screenshotter custom toolset,” the enterprise security firm said.
TA866 was first documented by the company in February 2023, attributing it to a campaign named Screentime that distributed WasabiSeed, a Visual Basic script dropper that’s used to download Screenshotter, which is capable of taking screenshots of the victim’s desktop at regular intervals of time and exfiltrating that data to an actor-controlled domain.
There is evidence to suggest that the organized actor may be financially motivated owing to the fact that Screenshotter acts as a recon tool to identify high-value targets for post-exploitation, and deploy an AutoHotKey (AHK)-based bot to ultimately drop the Rhadamanthys information stealer.
Subsequent findings from Slovak cybersecurity firm ESET in June 2023 unearthed overlaps between Screentime and another intrusion set dubbed Asylum Ambuscade, a crimeware group active since at least 2020 that also engages in cyber espionage operations.
The latest attack chain remains virtually unchanged save for the switch from macro-enabled Publisher attachments to PDFs bearing a rogue OneDrive link, with the campaign relying on a spam service provided by TA571 to distribute the booby-trapped PDFs.
“TA571 is a spam distributor, and this actor sends high volume spam email campaigns to deliver and install a variety of malware for their cybercriminal customers,” Proofpoint researcher Axel F said.
This includes AsyncRAT, NetSupport RAT, IcedID, PikaBot, QakBot (aka Qbot), and DarkGate, the last of which allows attackers to perform various commands such as information theft, cryptocurrency mining, and execution of arbitrary programs.
“Darkgate…