Tag Archive for: Desktop
3CX customers targeted via trojanized desktop app
/in Mobile Security
Suspected state-sponsored threat actors have trojanized the official Windows desktop app of the widely used 3CX softphone solution, a number of cybersecurity companies began warning on Wednesday.
What is 3CX?
3CX is Voice over Internet Protocol (VoIP) private automatic branch exchange (PABX) software that provides video conferencing and live chat capabilities.
3CX offers a Windows, macOS, Linux, Android and iOS version of the app, a Chrome extension, and the PWA (progressive web app) version so the software can be also used via any browser.
The company lists many high-profile companies and organizations among its 600,000+ enterprise customers.
What happened?
3CX CISO Pierre Jourdan says that the Windows version of the 3CX client app (based on the Electron framework) has been injected with malware, advised users to uninstall the app for the time being and use the PWA version until they are able to push out a clean version.
But Trend Micro and Crowdstrike researchers say that macOS versions of the 3CX desktop app have been trojanized, as well. More specifically, these files:
- 3cxdesktopapp-18.12.407.msi (Windows)
- 3cxdesktopapp-18.12.416.msi (Windows)
- 3CXDesktopApp-18.11.1213.dmg (macOS)
- 3cxdesktopapp-latest.dmg (macOS)
So, until 3CX finish their investigation and we know more, customers would do well to find and uninstall them. Both companies (and Sophos, and SentinelOne) have provided indicators or compromise 3CX customers can use to find evidence of compromise on their systems.
It’s still unclear how far back the trojanized versions began to get served to customers but, as Satnam Narang, staff research engineer at Tenable, pointed out, “3CX customers reported receiving threat alerts from SentinelOne as early as March 22.”
Who’s behind it?
3CX’s investigation will hopefully soon reveal the exact moment their legitimate apps have been switched with trojanized ones, and will be able to share how their delivery infrastructure has been compromised.
In the meantime, potentially affected customers should know that the malicious apps:
- Contacted various C2 servers
- Retrieved a second-stage payload hosted on a public GitHub repository, which then
- Downloaded info-stealing…
CISA Warns Of Heightened Hacking Threat Using Legit Remote Desktop Tools
/in Computer Security
RMM software, similar to remote desktop software, provides users with a set of tools to remotely access and manage computer systems. Unfortunately, as we reported recently, threat actors have taken to using this legitimate software in place of malware to access victims’ devices. Since RMM software is also used by those providing authentic IT support, it can be difficult for users to distinguish between legitimate and malicious uses of this software, particularly when threat actors pose as IT support technicians.
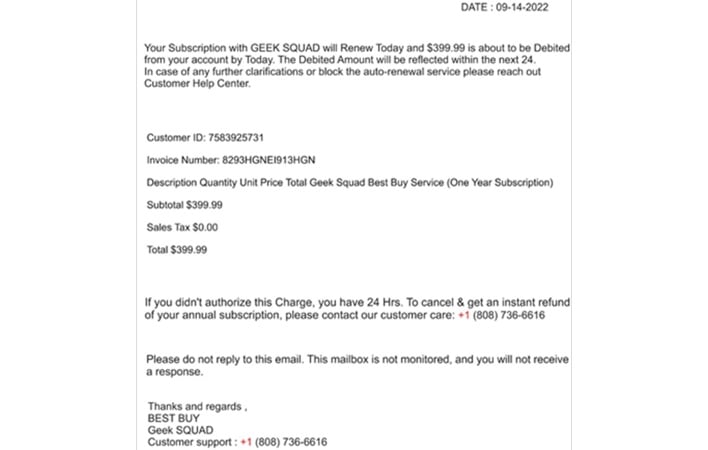
These websites served RMM software executables to visitors under the pretense that customer support agents would use the software to help resolve problems with the invoice refund process. Since portable executables skip the installation process and directly launch programs, the RMM software distributed by the threat actors could bypass security controls blocking the installation of unapproved programs. The RMM software, whether AnyDesk or ScreenConnect, was configured to automatically connect to the threat actor’s RMM servers, giving the threat actors access to victims’ computers shortly after launching.
Once the RMM software was running, the threat…